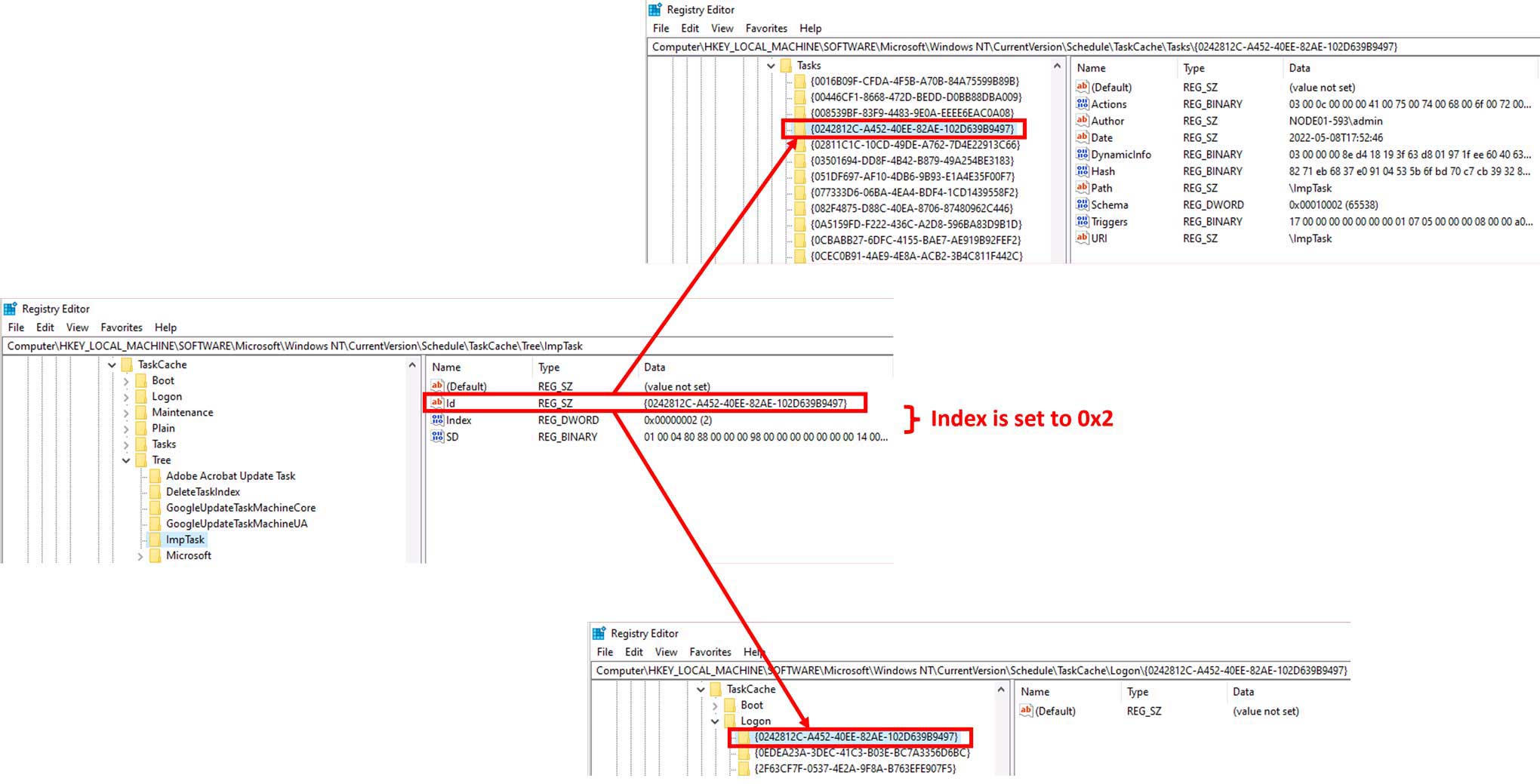
Hide Schedule Task Via Index Value Tamper
Detects when the "index" value of a scheduled task is modified from the registry Which effectively hides it from any tooling such as "schtasks /query" (Read the referenced link for more information about the effects of this technique)
Sigma rule (View on GitHub)
1title: Hide Schedule Task Via Index Value Tamper
2id: 5b16df71-8615-4f7f-ac9b-6c43c0509e61
3related:
4 - id: acd74772-5f88-45c7-956b-6a7b36c294d2
5 type: similar
6 - id: 526cc8bc-1cdc-48ad-8b26-f19bff969cec
7 type: similar
8status: test
9description: |
10 Detects when the "index" value of a scheduled task is modified from the registry
11 Which effectively hides it from any tooling such as "schtasks /query" (Read the referenced link for more information about the effects of this technique)
12references:
13 - https://blog.qualys.com/vulnerabilities-threat-research/2022/06/20/defending-against-scheduled-task-attacks-in-windows-environments
14author: Nasreddine Bencherchali (Nextron Systems)
15date: 2022-08-26
16modified: 2023-08-17
17tags:
18 - attack.defense-evasion
19 - attack.t1562
20logsource:
21 category: registry_set
22 product: windows
23detection:
24 selection:
25 TargetObject|contains|all:
26 - '\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\'
27 - 'Index'
28 Details: DWORD (0x00000000)
29 condition: selection
30falsepositives:
31 - Unlikely
32level: high
References
Related rules
- Azure Kubernetes Events Deleted
- ETW Logging Tamper In .NET Processes Via CommandLine
- Google Cloud Firewall Modified or Deleted
- Sysmon Application Crashed
- Sysmon Driver Unloaded Via Fltmc.EXE