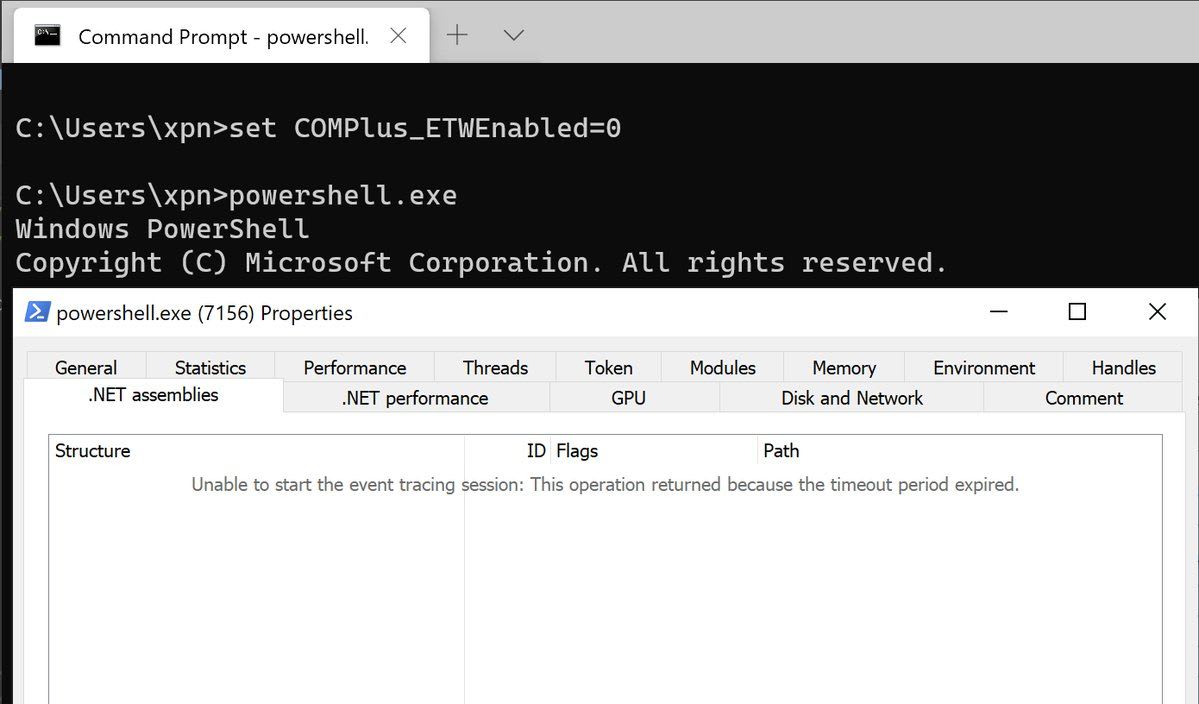
ETW Logging Disabled In .NET Processes - Sysmon Registry
Potential adversaries stopping ETW providers recording loaded .NET assemblies.
Sigma rule (View on GitHub)
1title: ETW Logging Disabled In .NET Processes - Sysmon Registry
2id: bf4fc428-dcc3-4bbd-99fe-2422aeee2544
3related:
4 - id: a4c90ea1-2634-4ca0-adbb-35eae169b6fc
5 type: similar
6status: test
7description: Potential adversaries stopping ETW providers recording loaded .NET assemblies.
8references:
9 - https://twitter.com/_xpn_/status/1268712093928378368
10 - https://social.msdn.microsoft.com/Forums/vstudio/en-US/0878832e-39d7-4eaf-8e16-a729c4c40975/what-can-i-use-e13c0d23ccbc4e12931bd9cc2eee27e4-for?forum=clr
11 - https://github.com/dotnet/runtime/blob/ee2355c801d892f2894b0f7b14a20e6cc50e0e54/docs/design/coreclr/jit/viewing-jit-dumps.md#setting-configuration-variables
12 - https://github.com/dotnet/runtime/blob/f62e93416a1799aecc6b0947adad55a0d9870732/src/coreclr/src/inc/clrconfigvalues.h#L35-L38
13 - https://github.com/dotnet/runtime/blob/7abe42dc1123722ed385218268bb9fe04556e3d3/src/coreclr/src/inc/clrconfig.h#L33-L39
14 - https://github.com/dotnet/runtime/search?p=1&q=COMPlus_&unscoped_q=COMPlus_
15 - https://bunnyinside.com/?term=f71e8cb9c76a
16 - http://managed670.rssing.com/chan-5590147/all_p1.html
17 - https://github.com/dotnet/runtime/blob/4f9ae42d861fcb4be2fcd5d3d55d5f227d30e723/docs/coding-guidelines/clr-jit-coding-conventions.md#1412-disabling-code
18 - https://blog.xpnsec.com/hiding-your-dotnet-complus-etwenabled/
19 - https://i.blackhat.com/EU-21/Wednesday/EU-21-Teodorescu-Veni-No-Vidi-No-Vici-Attacks-On-ETW-Blind-EDRs.pdf
20author: Roberto Rodriguez (Cyb3rWard0g), OTR (Open Threat Research)
21date: 2020-06-05
22modified: 2023-08-17
23tags:
24 - attack.persistence
25 - attack.defense-evasion
26 - attack.t1112
27 - attack.t1562
28logsource:
29 product: windows
30 category: registry_set
31detection:
32 selection_etw_enabled:
33 TargetObject|endswith: 'SOFTWARE\Microsoft\.NETFramework\ETWEnabled'
34 Details: 'DWORD (0x00000000)'
35 selection_complus:
36 TargetObject|endswith:
37 - '\COMPlus_ETWEnabled'
38 - '\COMPlus_ETWFlags'
39 Details:
40 - 0 # For REG_SZ type
41 - 'DWORD (0x00000000)'
42 condition: 1 of selection_*
43falsepositives:
44 - Unknown
45level: high
References
Related rules
- ETW Logging Disabled For SCM
- ETW Logging Disabled For rpcrt4.dll
- ETW Logging Disabled In .NET Processes - Registry
- Activate Suppression of Windows Security Center Notifications
- Add DisallowRun Execution to Registry