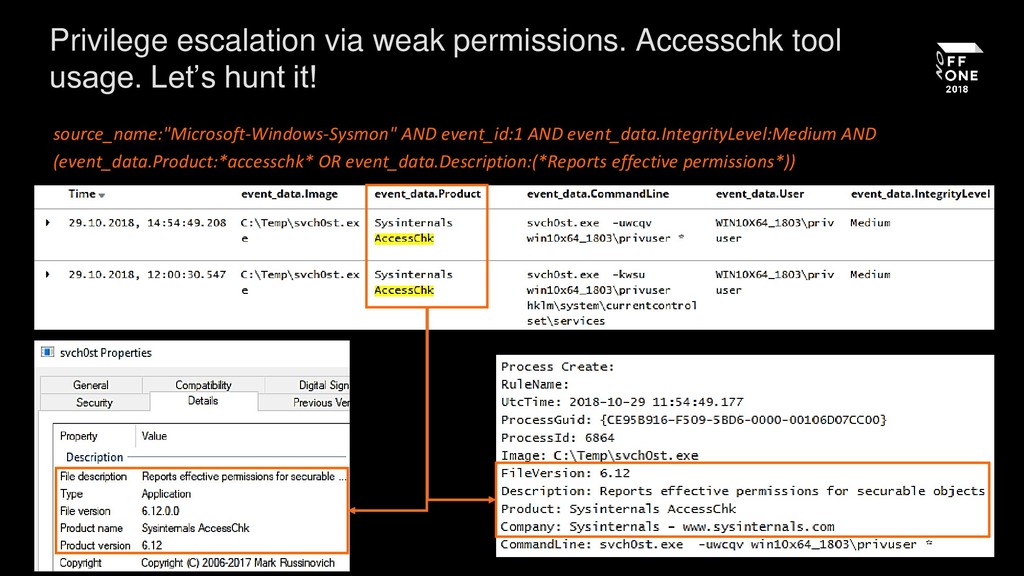
Permission Check Via Accesschk.EXE
Detects the usage of the "Accesschk" utility, an access and privilege audit tool developed by SysInternal and often being abused by attacker to verify process privileges
Sigma rule (View on GitHub)
1title: Permission Check Via Accesschk.EXE
2id: c625d754-6a3d-4f65-9c9a-536aea960d37
3status: test
4description: Detects the usage of the "Accesschk" utility, an access and privilege audit tool developed by SysInternal and often being abused by attacker to verify process privileges
5references:
6 - https://speakerdeck.com/heirhabarov/hunting-for-privilege-escalation-in-windows-environment?slide=43
7 - https://www.youtube.com/watch?v=JGs-aKf2OtU&ab_channel=OFFZONEMOSCOW
8 - https://github.com/carlospolop/PEASS-ng/blob/fa0f2e17fbc1d86f1fd66338a40e665e7182501d/winPEAS/winPEASbat/winPEAS.bat
9 - https://github.com/gladiatx0r/Powerless/blob/04f553bbc0c65baf4e57344deff84e3f016e6b51/Powerless.bat
10author: Teymur Kheirkhabarov (idea), Mangatas Tondang, oscd.community, Nasreddine Bencherchali (Nextron Systems)
11date: 2020-10-13
12modified: 2023-02-20
13tags:
14 - attack.discovery
15 - attack.t1069.001
16logsource:
17 product: windows
18 category: process_creation
19detection:
20 selection_img:
21 - Product|endswith: 'AccessChk'
22 - Description|contains: 'Reports effective permissions'
23 - Image|endswith:
24 - '\accesschk.exe'
25 - '\accesschk64.exe'
26 - OriginalFileName: 'accesschk.exe'
27 selection_cli:
28 CommandLine|contains: # These are the most common flags used with this tool. You could add other combinations if needed
29 - 'uwcqv '
30 - 'kwsu '
31 - 'qwsu '
32 - 'uwdqs '
33 condition: all of selection*
34falsepositives:
35 - System administrator Usage
36level: medium
References
Related rules
- AD Groups Or Users Enumeration Using PowerShell - PoshModule
- AD Groups Or Users Enumeration Using PowerShell - ScriptBlock
- HackTool - Bloodhound/Sharphound Execution
- Local Groups Discovery - MacOs
- Local Groups Reconnaissance Via Wmic.EXE