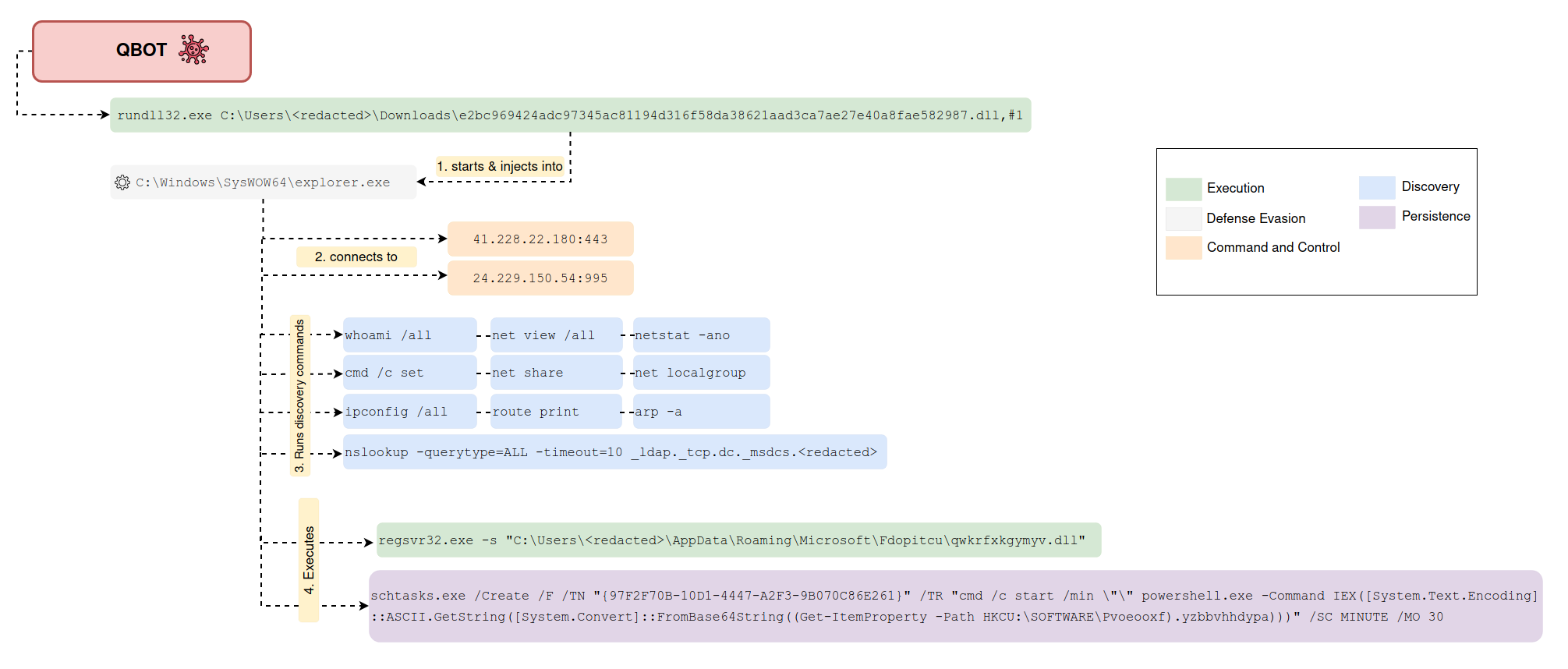
Scheduled Task Executing Encoded Payload from Registry
Detects the creation of a schtask that potentially executes a base64 encoded payload stored in the Windows Registry using PowerShell.
Sigma rule (View on GitHub)
1title: Scheduled Task Executing Encoded Payload from Registry
2id: c4eeeeae-89f4-43a7-8b48-8d1bdfa66c78
3status: test
4description: Detects the creation of a schtask that potentially executes a base64 encoded payload stored in the Windows Registry using PowerShell.
5references:
6 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
7author: pH-T (Nextron Systems), @Kostastsale, TheDFIRReport, X__Junior (Nextron Systems), Nasreddine Bencherchali (Nextron Systems)
8date: 2022-02-12
9modified: 2023-02-04
10tags:
11 - attack.privilege-escalation
12 - attack.execution
13 - attack.persistence
14 - attack.t1053.005
15 - attack.t1059.001
16logsource:
17 product: windows
18 category: process_creation
19detection:
20 selection_img:
21 # schtasks.exe /Create /F /TN "{97F2F70B-10D1-4447-A2F3-9B070C86E261}" /TR "cmd /c start /min \"\" powershell.exe -Command IEX([System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String((Get-ItemProperty -Path HKCU:\SOFTWARE\Pvoeooxf).yzbbvhhdypa))) " /SC MINUTE /MO 30
22 - Image|endswith: '\schtasks.exe'
23 - OriginalFileName: 'schtasks.exe'
24 selection_cli_create:
25 CommandLine|contains: '/Create'
26 selection_cli_encoding:
27 CommandLine|contains:
28 - 'FromBase64String'
29 - 'encodedcommand'
30 selection_cli_get:
31 CommandLine|contains:
32 - 'Get-ItemProperty'
33 - ' gp ' # Alias
34 selection_cli_hive:
35 CommandLine|contains:
36 - 'HKCU:'
37 - 'HKLM:'
38 - 'registry::'
39 - 'HKEY_'
40 condition: all of selection_*
41falsepositives:
42 - Unlikely
43level: high
References
Related rules
- ChromeLoader Malware Execution
- Operation Wocao Activity
- Operation Wocao Activity - Security
- Potential Persistence Via Powershell Search Order Hijacking - Task
- Scheduled Task Executing Payload from Registry