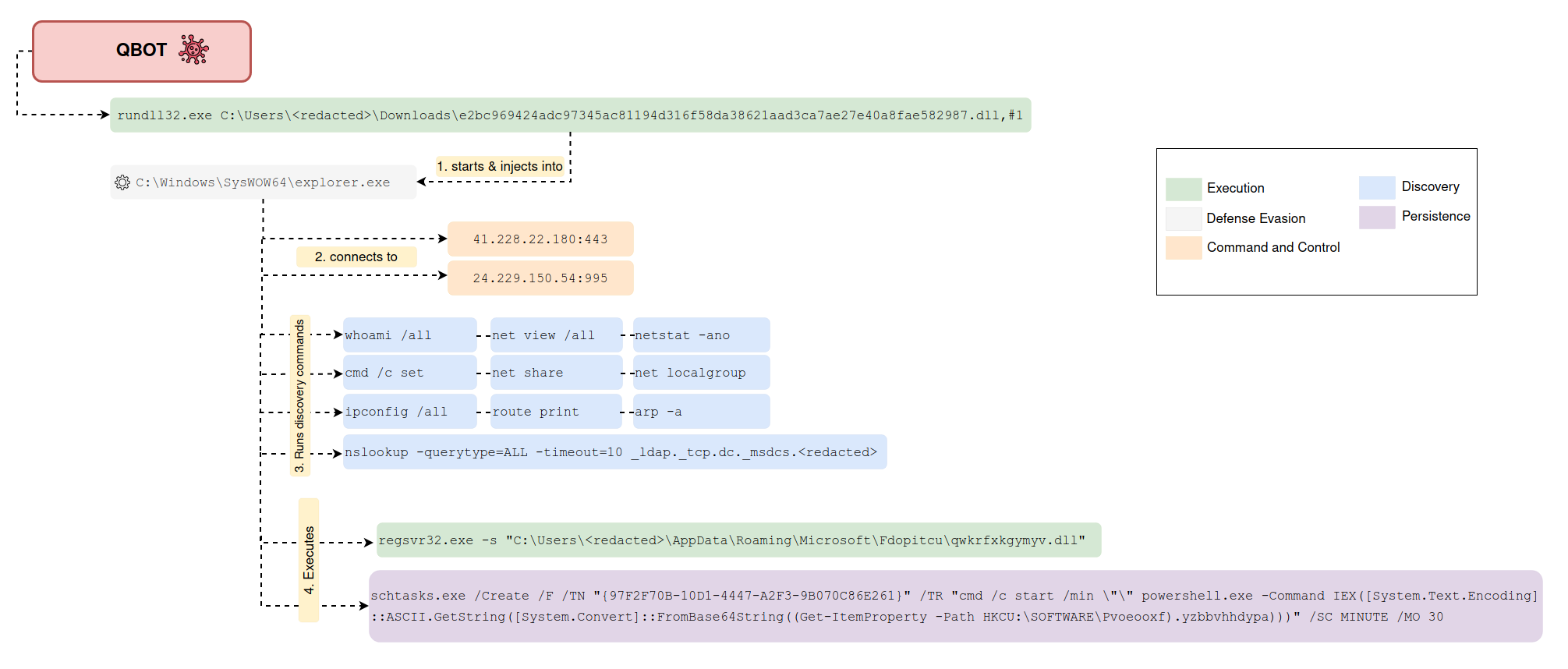
Potential Tampering With RDP Related Registry Keys Via Reg.EXE
Detects the execution of "reg.exe" for enabling/disabling the RDP service on the host by tampering with the 'CurrentControlSet\Control\Terminal Server' values
Sigma rule (View on GitHub)
1title: Potential Tampering With RDP Related Registry Keys Via Reg.EXE
2id: 0d5675be-bc88-4172-86d3-1e96a4476536
3status: test
4description: Detects the execution of "reg.exe" for enabling/disabling the RDP service on the host by tampering with the 'CurrentControlSet\Control\Terminal Server' values
5references:
6 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
7 - http://etutorials.org/Microsoft+Products/microsoft+windows+server+2003+terminal+services/Chapter+6+Registry/Registry+Keys+for+Terminal+Services/ # Contain description for most of the keys mentioned here (check it out if you want more information
8 - http://woshub.com/rds-shadow-how-to-connect-to-a-user-session-in-windows-server-2012-r2/ # Related to the Shadow RPD technique
9 - https://admx.help/HKLM/SOFTWARE/Policies/Microsoft/Windows%20NT/Terminal%20Services # Contain description for most of the keys mentioned here (check it out if you want more information)
10 - https://bazaar.abuse.ch/sample/6f3aa9362d72e806490a8abce245331030d1ab5ac77e400dd475748236a6cc81/
11 - https://blog.sekoia.io/darkgate-internals/
12 - https://blog.talosintelligence.com/understanding-the-phobos-affiliate-structure/
13 - https://github.com/redcanaryco/atomic-red-team/blob/02c7d02fe1f1feb0fc7944550408ea8224273994/atomics/T1112/T1112.md#atomic-test-63---disable-remote-desktop-anti-alias-setting-through-registry
14 - https://github.com/redcanaryco/atomic-red-team/blob/02c7d02fe1f1feb0fc7944550408ea8224273994/atomics/T1112/T1112.md#atomic-test-64---disable-remote-desktop-security-settings-through-registry
15 - https://github.com/redcanaryco/atomic-red-team/blob/dd526047b8c399c312fee47d1e6fb531164da54d/atomics/T1112/T1112.yaml#L790
16 - https://learn.microsoft.com/en-us/windows-hardware/customize/desktop/unattend/microsoft-windows-terminalservices-rdp-winstationextensions-securitylayer
17 - https://threathunterplaybook.com/hunts/windows/190407-RegModEnableRDPConnections/notebook.html
18 - https://twitter.com/SagieSec/status/1469001618863624194?t=HRf0eA0W1YYzkTSHb-Ky1A&s=03 # Related to the Shadow RPD technique
19 - https://web.archive.org/web/20200929062532/https://blog.menasec.net/2019/02/threat-hunting-rdp-hijacking-via.html # Related to RDP hijacking via the "ServiceDll" key
20 - https://www.trendmicro.com/en_us/research/25/i/unmasking-the-gentlemen-ransomware.html
21author: pH-T (Nextron Systems), @Kostastsale, TheDFIRReport
22date: 2022-02-12
23modified: 2025-11-22
24tags:
25 - attack.persistence
26 - attack.defense-evasion
27 - attack.lateral-movement
28 - attack.t1021.001
29 - attack.t1112
30logsource:
31 product: windows
32 category: process_creation
33detection:
34 selection_main_img:
35 - Image|endswith: '\reg.exe'
36 - OriginalFileName: 'reg.exe'
37 selection_main_cli:
38 CommandLine|contains|all:
39 - ' add '
40 - '\CurrentControlSet\Control\Terminal Server'
41 - 'REG_DWORD'
42 - ' /f'
43 selection_values_1:
44 CommandLine|contains|all:
45 - 'Licensing Core'
46 - 'EnableConcurrentSessions'
47 selection_values_2:
48 CommandLine|contains:
49 - 'AllowTSConnections'
50 - 'fDenyTSConnections'
51 - 'fEnableWinStation'
52 - 'fSingleSessionPerUser'
53 - 'IdleWinStationPoolCount'
54 - 'MaxInstanceCount'
55 - 'SecurityLayer'
56 - 'TSAdvertise'
57 - 'TSAppCompat'
58 - 'TSEnabled'
59 - 'TSUserEnabled'
60 - 'WinStations\RDP-Tcp'
61 filter_main_values_tls:
62 CommandLine|contains|all:
63 - 'SecurityLayer'
64 - '02' # TLS Enabled
65 condition: all of selection_main_* and 1 of selection_values_* and not 1 of filter_main_*
66falsepositives:
67 - Unknown
68level: high
References
Related rules
- Remote Registry Lateral Movement
- RDP Sensitive Settings Changed
- Registry Modification Attempt Via VBScript
- Registry Modification Attempt Via VBScript - PowerShell
- Registry Tampering by Potentially Suspicious Processes