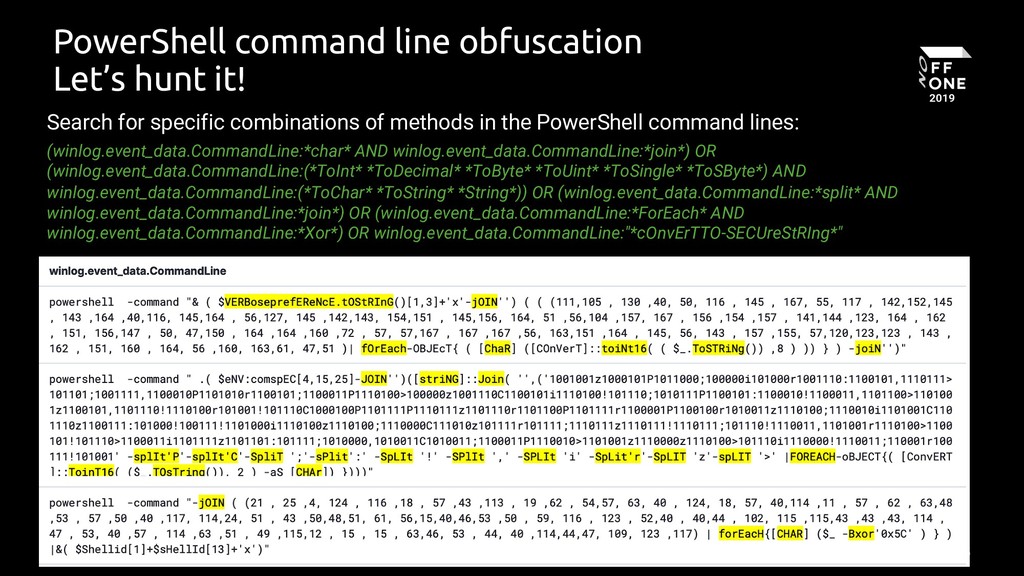
Suspicious XOR Encoded PowerShell Command
Detects presence of a potentially xor encoded powershell command
Sigma rule (View on GitHub)
1title: Suspicious XOR Encoded PowerShell Command
2id: bb780e0c-16cf-4383-8383-1e5471db6cf9
3related:
4 - id: 5b572dcf-254b-425c-a8c5-d9af6bea35a6
5 type: obsolete
6status: test
7description: Detects presence of a potentially xor encoded powershell command
8references:
9 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=65
10 - https://redcanary.com/blog/yellow-cockatoo/
11 - https://zero2auto.com/2020/05/19/netwalker-re/
12 - https://mez0.cc/posts/cobaltstrike-powershell-exec/
13author: Sami Ruohonen, Harish Segar, Tim Shelton, Teymur Kheirkhabarov, Vasiliy Burov, oscd.community, Nasreddine Bencherchali
14date: 2018-09-05
15modified: 2023-01-30
16tags:
17 - attack.defense-evasion
18 - attack.execution
19 - attack.t1059.001
20 - attack.t1140
21 - attack.t1027
22logsource:
23 category: process_creation
24 product: windows
25detection:
26 selection_img:
27 - Image|endswith:
28 - '\powershell.exe'
29 - '\pwsh.exe'
30 - OriginalFileName:
31 - 'PowerShell.EXE'
32 - 'pwsh.dll'
33 - Description: 'Windows PowerShell'
34 - Product: 'PowerShell Core 6'
35 selection_cli_xor:
36 CommandLine|contains: 'bxor'
37 selection_cli_other:
38 CommandLine|contains:
39 - 'ForEach'
40 - 'for('
41 - 'for '
42 - '-join '
43 - "-join'"
44 - '-join"'
45 - '-join`'
46 - '::Join'
47 - '[char]'
48 condition: all of selection_*
49falsepositives:
50 - Unknown
51level: medium
References
Related rules
- ConvertTo-SecureString Cmdlet Usage Via CommandLine
- Invoke-Obfuscation CLIP+ Launcher
- Invoke-Obfuscation CLIP+ Launcher - PowerShell
- Invoke-Obfuscation CLIP+ Launcher - PowerShell Module
- Invoke-Obfuscation CLIP+ Launcher - Security