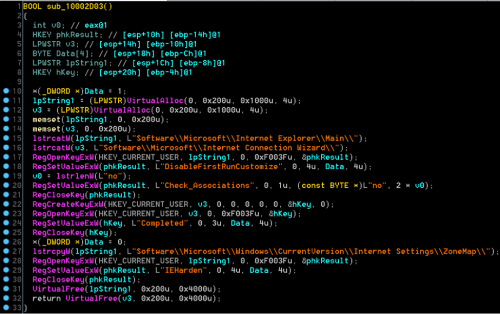
Disabled IE Security Features
Detects command lines that indicate unwanted modifications to registry keys that disable important Internet Explorer security features
Sigma rule (View on GitHub)
1title: Disabled IE Security Features
2id: fb50eb7a-5ab1-43ae-bcc9-091818cb8424
3status: test
4description: Detects command lines that indicate unwanted modifications to registry keys that disable important Internet Explorer security features
5references:
6 - https://unit42.paloaltonetworks.com/operation-ke3chang-resurfaces-with-new-tidepool-malware/
7author: Florian Roth (Nextron Systems)
8date: 2020-06-19
9modified: 2021-11-27
10tags:
11 - attack.defense-evasion
12 - attack.t1562.001
13logsource:
14 category: process_creation
15 product: windows
16detection:
17 selection1:
18 CommandLine|contains|all:
19 - ' -name IEHarden '
20 - ' -value 0 '
21 selection2:
22 CommandLine|contains|all:
23 - ' -name DEPOff '
24 - ' -value 1 '
25 selection3:
26 CommandLine|contains|all:
27 - ' -name DisableFirstRunCustomize '
28 - ' -value 2 '
29 condition: 1 of selection*
30falsepositives:
31 - Unknown
32level: high
References
Related rules
- AMSI Bypass Pattern Assembly GetType
- AWS GuardDuty Important Change
- Azure Kubernetes Events Deleted
- Disable Exploit Guard Network Protection on Windows Defender
- Disable PUA Protection on Windows Defender