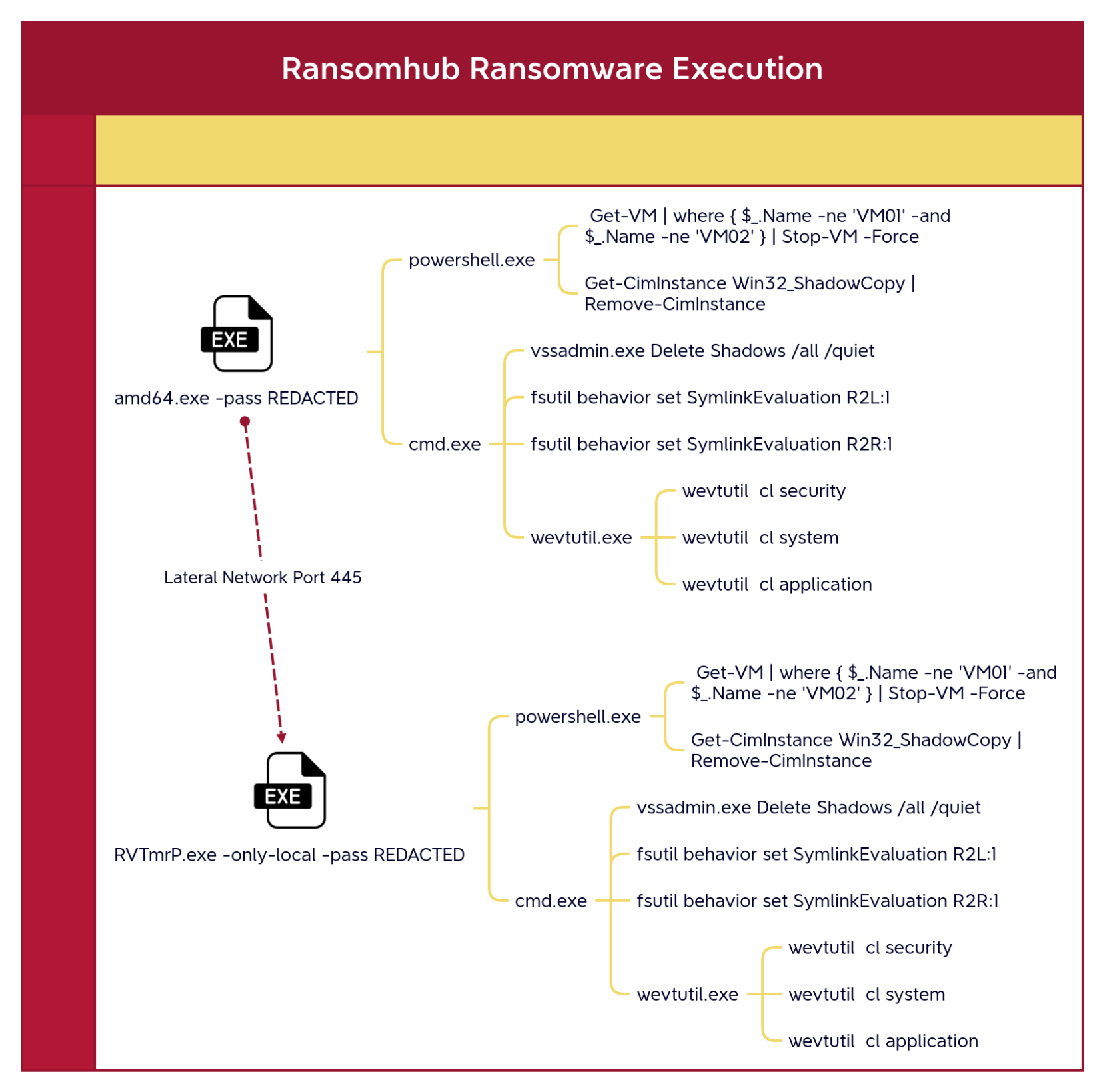
Potentially Suspicious NTFS Symlink Behavior Modification
Detects the modification of NTFS symbolic link behavior using fsutil, which could be used to enable remote to local or remote to remote symlinks for potential attacks.
Sigma rule (View on GitHub)
1title: Potentially Suspicious NTFS Symlink Behavior Modification
2id: c0b2768a-dd06-4671-8339-b16ca8d1f27f
3status: test
4description: |
5 Detects the modification of NTFS symbolic link behavior using fsutil, which could be used to enable remote to local or remote to remote symlinks for potential attacks.
6references:
7 - https://www.cybereason.com/blog/cybereason-vs.-blackcat-ransomware
8 - https://learn.microsoft.com/fr-fr/windows-server/administration/windows-commands/fsutil-behavior
9 - https://thedfirreport.com/2025/06/30/hide-your-rdp-password-spray-leads-to-ransomhub-deployment/
10author: frack113, The DFIR Report
11date: 2022-03-02
12modified: 2025-11-13
13tags:
14 - attack.execution
15 - attack.t1059
16 - attack.defense-evasion
17 - attack.t1222.001
18logsource:
19 category: process_creation
20 product: windows
21detection:
22 selection_img_proxy:
23 # Note: Example command observed: cmd.exe /c "fsutil behaviour set SymlinkEvaluation"
24 - Image|endswith:
25 - '\cmd.exe'
26 - '\powershell.exe'
27 - '\pwsh.exe'
28 - OriginalFileName:
29 - 'Cmd.Exe'
30 - 'PowerShell.EXE'
31 - 'pwsh.dll'
32 selection_fsutil_cli:
33 CommandLine|contains|all:
34 - 'fsutil'
35 - 'behavior'
36 - 'set'
37 - 'SymlinkEvaluation'
38 selection_symlink_params:
39 CommandLine|contains:
40 - 'R2L:1' # Remote to Local
41 - 'R2R:1' # Remote to Remote
42 - 'L2L:1' # Local to Local
43 condition: all of selection_*
44falsepositives:
45 - Legitimate usage, investigate the parent process and context to determine if benign.
46level: medium
References
Related rules
- Hacktool Ruler
- Potential Arbitrary Command Execution Via FTP.EXE
- Writing Of Malicious Files To The Fonts Folder
- Outlook EnableUnsafeClientMailRules Setting Enabled
- Suspicious Remote Child Process From Outlook