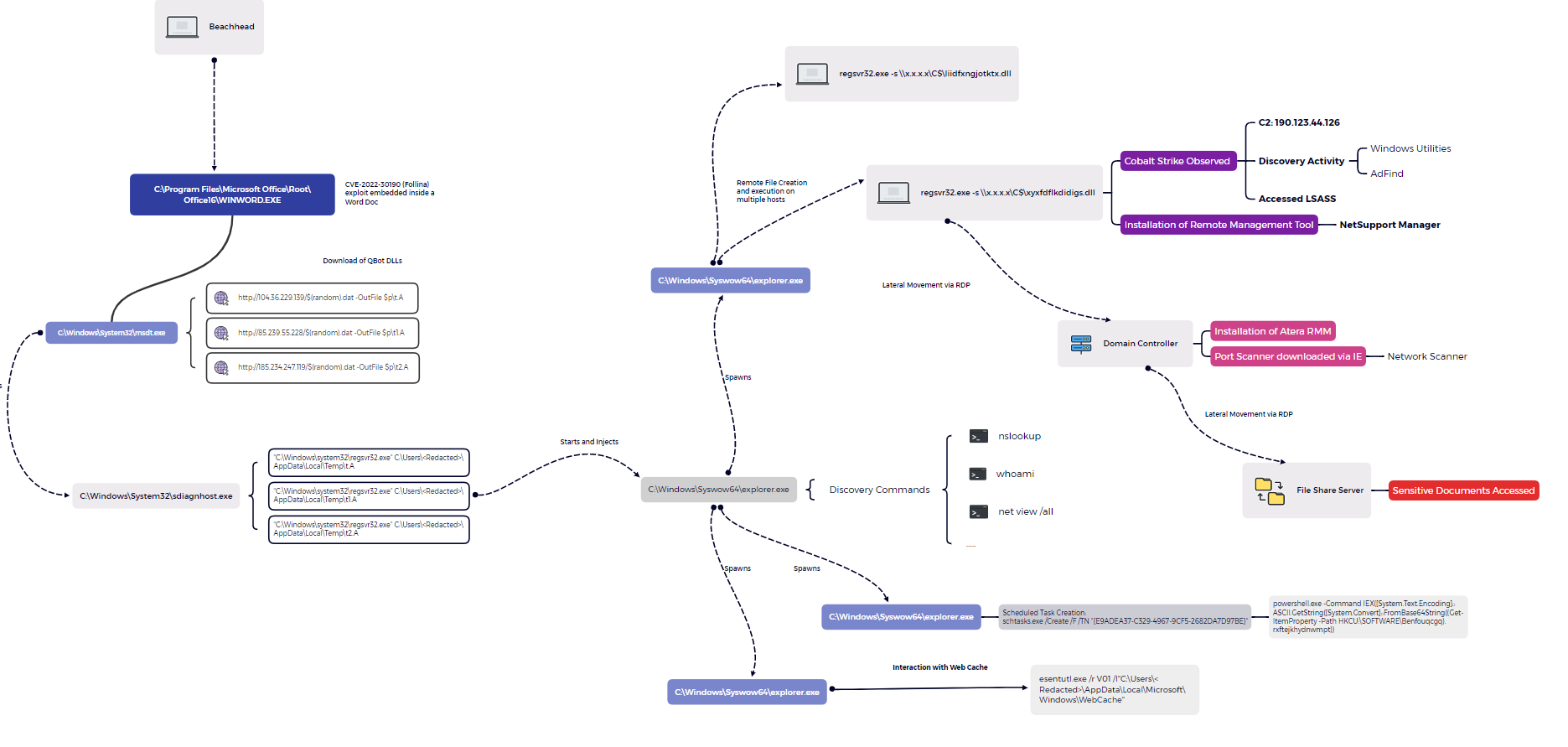
Esentutl Steals Browser Information
One way Qbot steals sensitive information is by extracting browser data from Internet Explorer and Microsoft Edge by using the built-in utility esentutl.exe
Sigma rule (View on GitHub)
1title: Esentutl Steals Browser Information
2id: 6a69f62d-ce75-4b57-8dce-6351eb55b362
3status: test
4description: One way Qbot steals sensitive information is by extracting browser data from Internet Explorer and Microsoft Edge by using the built-in utility esentutl.exe
5references:
6 - https://thedfirreport.com/2022/02/07/qbot-likes-to-move-it-move-it/
7 - https://redcanary.com/threat-detection-report/threats/qbot/
8 - https://thedfirreport.com/2022/10/31/follina-exploit-leads-to-domain-compromise/
9author: frack113
10date: 2022-02-13
11modified: 2024-03-05
12tags:
13 - attack.collection
14 - attack.t1005
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection_img:
20 - Image|endswith: '\esentutl.exe'
21 - OriginalFileName: 'esentutl.exe'
22 selection_flag:
23 CommandLine|contains|windash: '-r'
24 selection_webcache:
25 CommandLine|contains: '\Windows\WebCache'
26 condition: all of selection*
27falsepositives:
28 - Legitimate use
29level: medium
References
Related rules
- Crash Dump Created By Operating System
- OpenCanary - SMB File Open Request
- ADFS Database Named Pipe Connection By Uncommon Tool
- AWS EC2 VM Export Failure
- Cisco Collect Data