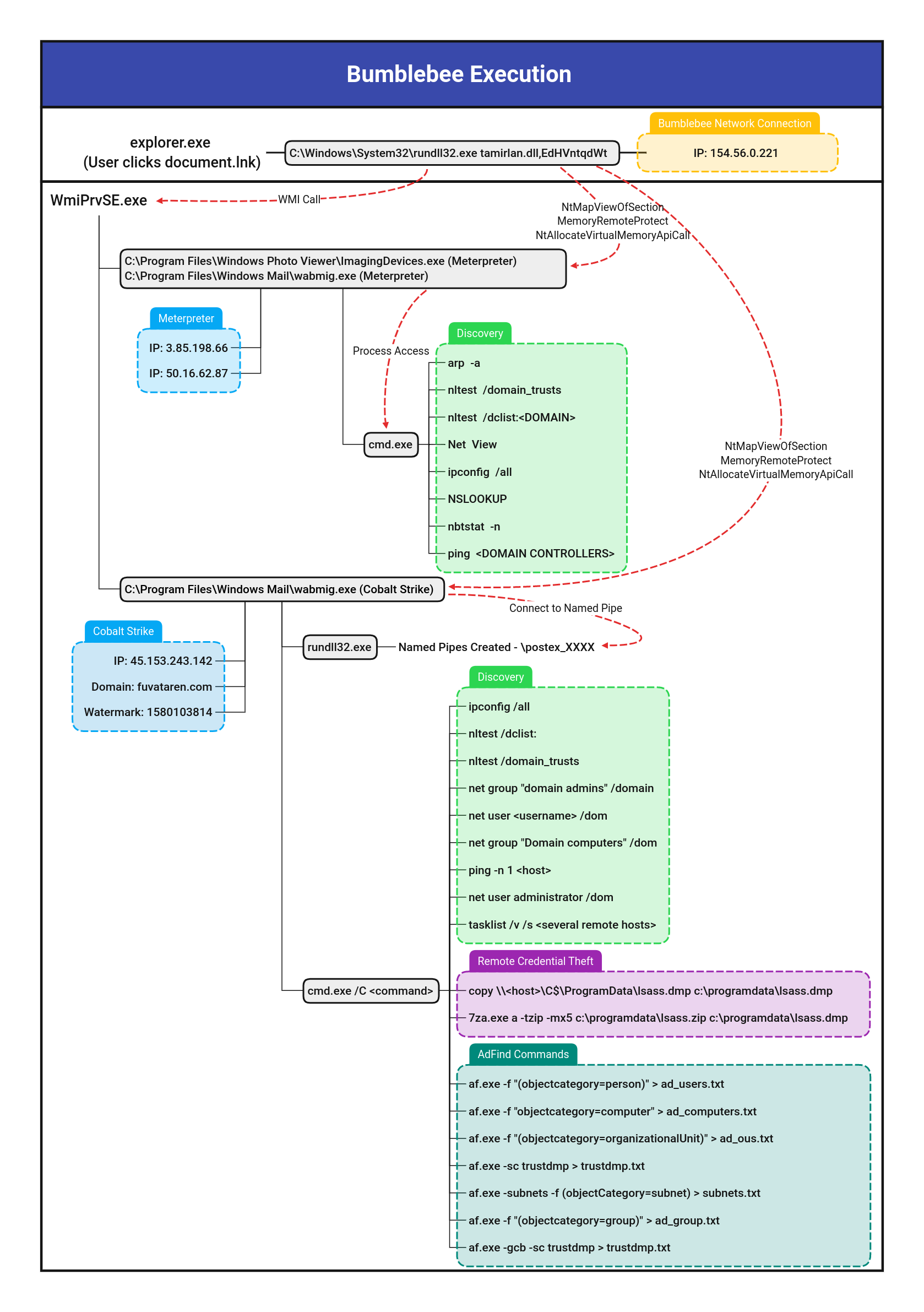
Copy .DMP/.DUMP Files From Remote Share Via Cmd.EXE
Detects usage of the copy builtin cmd command to copy files with the ".dmp"/".dump" extension from a remote share
Sigma rule (View on GitHub)
1title: Copy .DMP/.DUMP Files From Remote Share Via Cmd.EXE
2id: 044ba588-dff4-4918-9808-3f95e8160606
3status: test
4description: Detects usage of the copy builtin cmd command to copy files with the ".dmp"/".dump" extension from a remote share
5references:
6 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
7author: Nasreddine Bencherchali (Nextron Systems)
8date: 2022-09-27
9modified: 2023-09-12
10tags:
11 - attack.credential-access
12logsource:
13 category: process_creation
14 product: windows
15detection:
16 # Example: copy \\<host>\\<folder>\\process.dmp C:\Users\process.dmp
17 selection_img:
18 - Image|endswith: '\cmd.exe'
19 - OriginalFileName: 'Cmd.Exe'
20 selection_cli:
21 CommandLine|contains|all:
22 - 'copy '
23 - ' \\\\'
24 CommandLine|contains:
25 - '.dmp'
26 - '.dump'
27 - '.hdmp'
28 condition: all of selection_*
29falsepositives:
30 - Unknown
31level: high
References
Related rules
- ADCS Certificate Template Configuration Vulnerability
- ADCS Certificate Template Configuration Vulnerability with Risky EKU
- Access to Browser Login Data
- Account Lockout
- Added Owner To Application