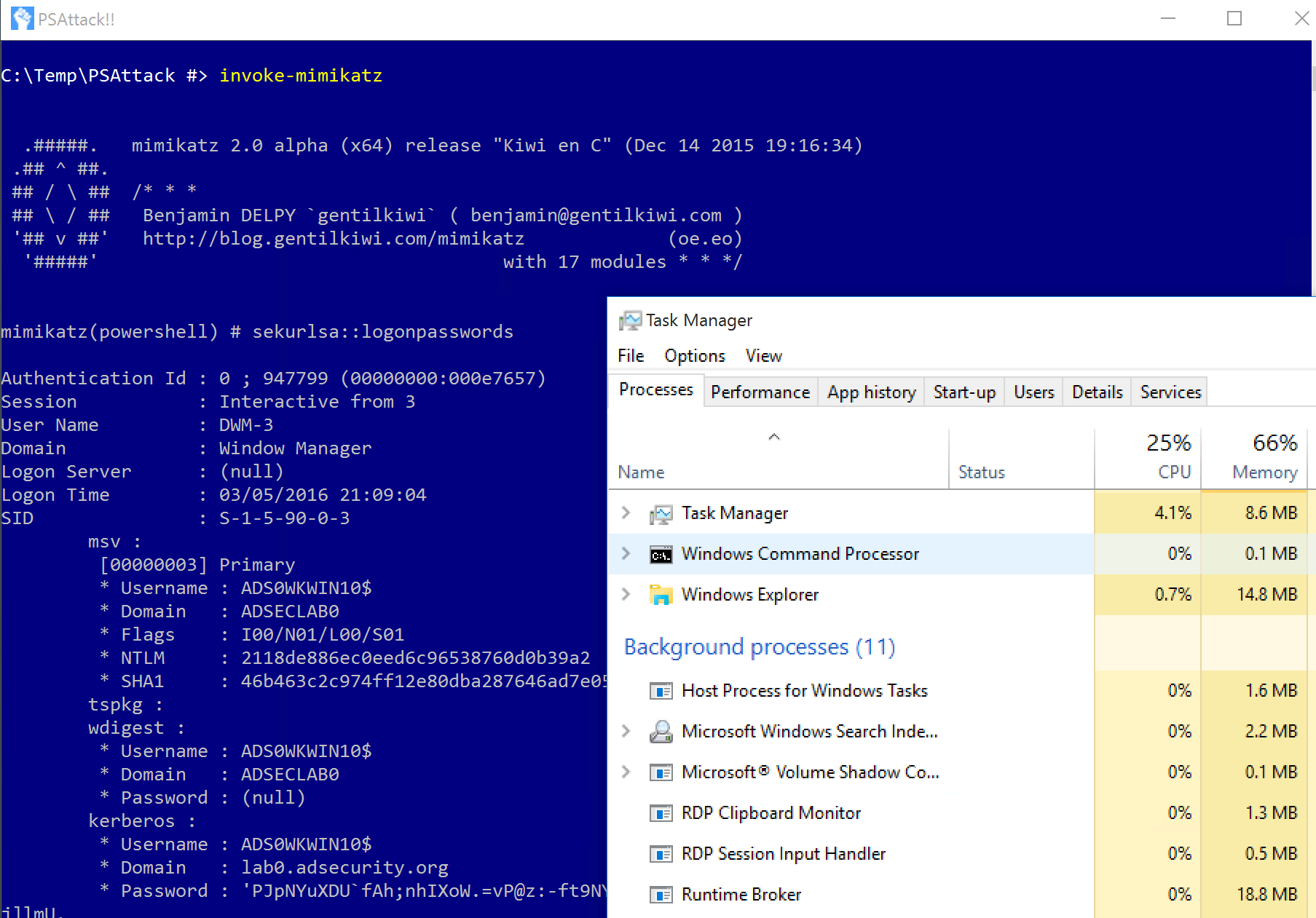
Malicious PowerShell Keywords
Detects keywords from well-known PowerShell exploitation frameworks
Sigma rule (View on GitHub)
1title: Malicious PowerShell Keywords
2id: f62176f3-8128-4faa-bf6c-83261322e5eb
3status: test
4description: Detects keywords from well-known PowerShell exploitation frameworks
5references:
6 - https://adsecurity.org/?p=2921
7author: Sean Metcalf (source), Florian Roth (Nextron Systems)
8date: 2017-03-05
9modified: 2023-06-20
10tags:
11 - attack.execution
12 - attack.t1059.001
13logsource:
14 product: windows
15 category: ps_script
16 definition: 'Requirements: Script Block Logging must be enabled'
17detection:
18 selection:
19 ScriptBlockText|contains:
20 - 'AdjustTokenPrivileges'
21 - 'IMAGE_NT_OPTIONAL_HDR64_MAGIC'
22 # - 'LSA_UNICODE_STRING'
23 - 'Metasploit'
24 - 'Microsoft.Win32.UnsafeNativeMethods'
25 - 'Mimikatz'
26 - 'MiniDumpWriteDump'
27 - 'PAGE_EXECUTE_READ'
28 - 'ReadProcessMemory.Invoke'
29 - 'SE_PRIVILEGE_ENABLED'
30 - 'SECURITY_DELEGATION'
31 - 'TOKEN_ADJUST_PRIVILEGES'
32 - 'TOKEN_ALL_ACCESS'
33 - 'TOKEN_ASSIGN_PRIMARY'
34 - 'TOKEN_DUPLICATE'
35 - 'TOKEN_ELEVATION'
36 - 'TOKEN_IMPERSONATE'
37 - 'TOKEN_INFORMATION_CLASS'
38 - 'TOKEN_PRIVILEGES'
39 - 'TOKEN_QUERY'
40 condition: selection
41falsepositives:
42 - Depending on the scripts, this rule might require some initial tuning to fit the environment
43level: medium
References
Related rules
- AWS EC2 Startup Shell Script Change
- Bad Opsec Powershell Code Artifacts
- Certificate Exported Via PowerShell
- Change PowerShell Policies to an Insecure Level - PowerShell
- Cmd.EXE Missing Space Characters Execution Anomaly