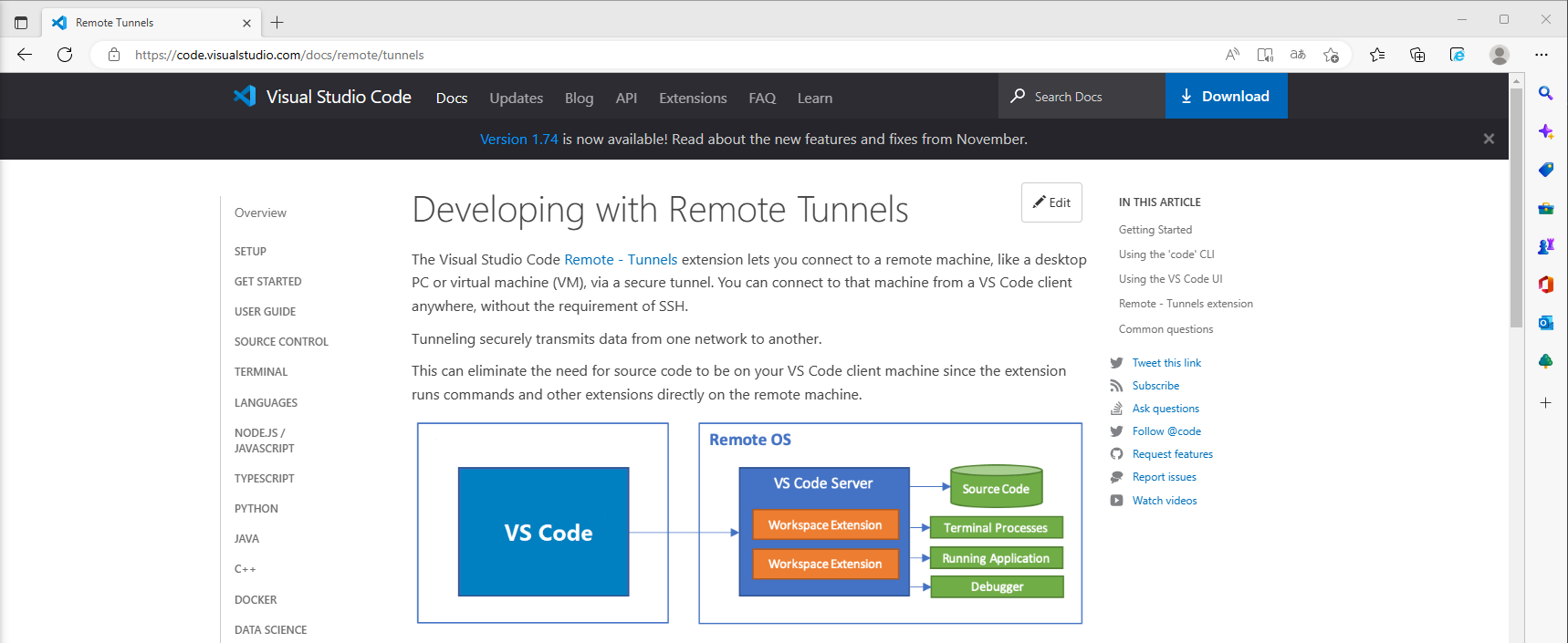
Network Connection Initiated To Visual Studio Code Tunnels Domain
Detects network connections to Visual Studio Code tunnel domains initiated by a process on a system. Attackers can abuse that feature to establish a reverse shell or persistence on a machine.
Sigma rule (View on GitHub)
1title: Network Connection Initiated To Visual Studio Code Tunnels Domain
2id: 4b657234-038e-4ad5-997c-4be42340bce4
3related:
4 - id: 9501f8e6-8e3d-48fc-a8a6-1089dd5d7ef4 # Net Connection DevTunnels
5 type: similar
6 - id: b3e6418f-7c7a-4fad-993a-93b65027a9f1 # DNS VsCode
7 type: similar
8 - id: 1cb0c6ce-3d00-44fc-ab9c-6d6d577bf20b # DNS DevTunnels
9 type: similar
10status: test
11description: |
12 Detects network connections to Visual Studio Code tunnel domains initiated by a process on a system. Attackers can abuse that feature to establish a reverse shell or persistence on a machine.
13references:
14 - https://ipfyx.fr/post/visual-studio-code-tunnel/
15 - https://badoption.eu/blog/2023/01/31/code_c2.html
16 - https://cydefops.com/vscode-data-exfiltration
17author: Kamran Saifullah
18date: 2023-11-20
19tags:
20 - attack.exfiltration
21 - attack.command-and-control
22 - attack.t1567
23 - attack.t1572
24logsource:
25 category: network_connection
26 product: windows
27detection:
28 selection:
29 Initiated: 'true'
30 DestinationHostname|endswith: '.tunnels.api.visualstudio.com'
31 condition: selection
32falsepositives:
33 - Legitimate use of Visual Studio Code tunnel will also trigger this.
34level: medium
References
Related rules
- Network Connection Initiated To Cloudflared Tunnels Domains
- Process Initiated Network Connection To Ngrok Domain
- Communication To Ngrok Tunneling Service - Linux
- Communication To Ngrok Tunneling Service Initiated
- Network Connection Initiated To DevTunnels Domain