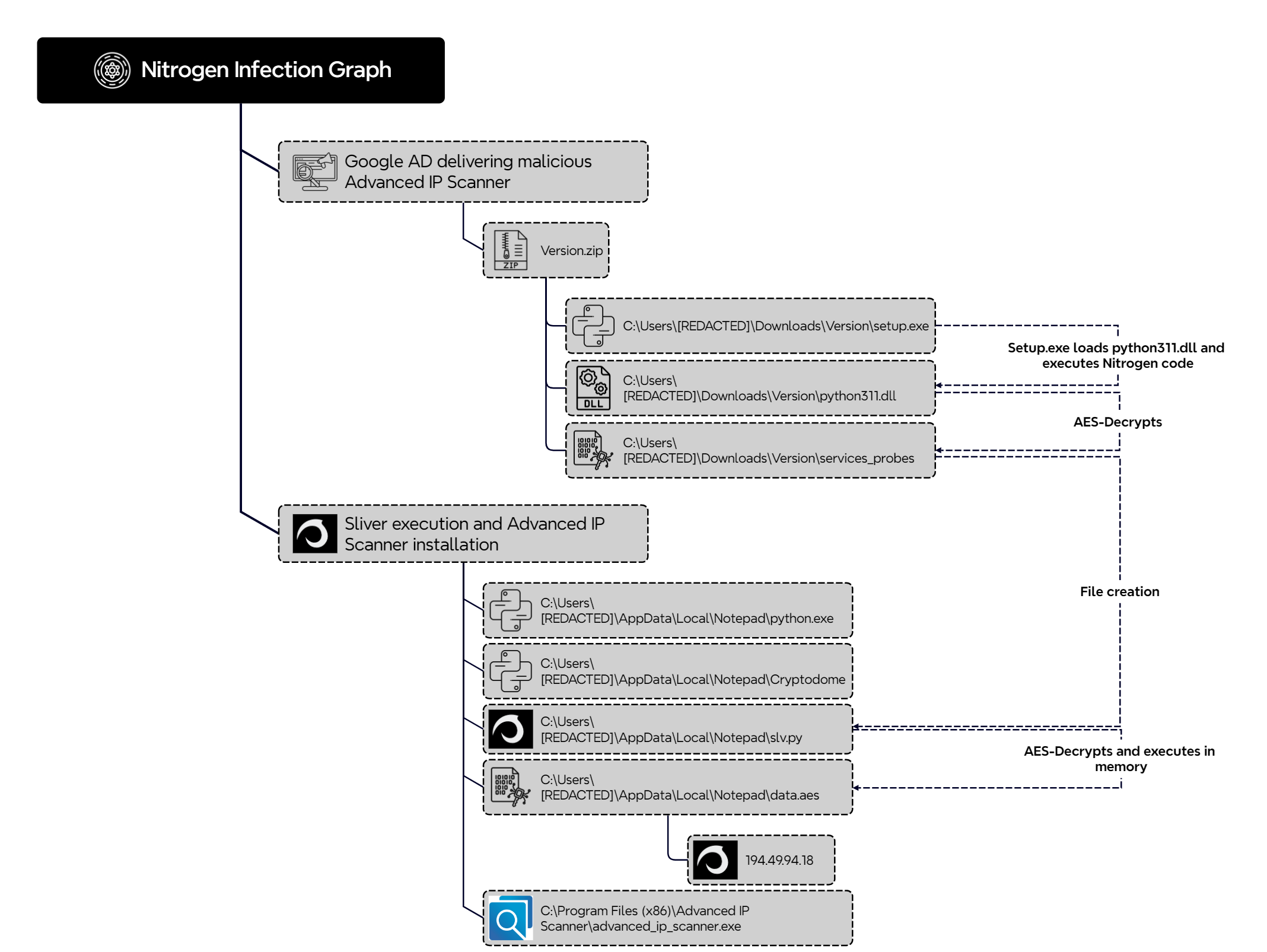
Potential Python DLL SideLoading
Detects potential DLL sideloading of Python DLL files.
Sigma rule (View on GitHub)
1title: Potential Python DLL SideLoading
2id: d36f7c12-14a3-4d48-b6b8-774b9c66f44d
3status: test
4description: Detects potential DLL sideloading of Python DLL files.
5references:
6 - https://www.securonix.com/blog/seolurker-attack-campaign-uses-seo-poisoning-fake-google-ads-to-install-malware/
7 - https://thedfirreport.com/2024/09/30/nitrogen-campaign-drops-sliver-and-ends-with-blackcat-ransomware/
8 - https://github.com/wietze/HijackLibs/tree/dc9c9f2f94e6872051dab58fbafb043fdd8b4176/yml/3rd_party/python
9author: Swachchhanda Shrawan Poudel
10date: 2024-10-06
11modified: 2025-08-18
12tags:
13 - attack.privilege-escalation
14 - attack.persistence
15 - attack.defense-evasion
16 - attack.t1574.001
17logsource:
18 category: image_load
19 product: windows
20detection:
21 selection:
22 ImageLoaded|endswith:
23 - '\python39.dll'
24 - '\python310.dll'
25 - '\python311.dll'
26 - '\python312.dll'
27 filter_main_default_install_paths:
28 - ImageLoaded|startswith:
29 - 'C:\Program Files\Python3'
30 - 'C:\Program Files (x86)\Python3'
31 - ImageLoaded|contains: '\AppData\Local\Programs\Python\Python3'
32 filter_optional_visual_studio:
33 ImageLoaded|startswith: 'C:\Program Files\Microsoft Visual Studio\'
34 filter_optional_anaconda:
35 ImageLoaded|startswith: 'C:\ProgramData\Anaconda3\' # Comment out if you don't use Anaconda in your environment
36 filter_optional_cpython:
37 ImageLoaded|contains:
38 - '\cpython\externals\'
39 - '\cpython\PCbuild\'
40 filter_optional_pyinstaller:
41 # Triggered by programs bundled with PyInstaller
42 ImageLoaded|startswith: 'C:\Users'
43 ImageLoaded|contains: '\AppData\Local\Temp\_MEI'
44 filter_main_legit_signature_details:
45 Product: 'Python'
46 Signed: 'true'
47 Description: 'Python'
48 Company: 'Python Software Foundation'
49 condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
50falsepositives:
51 - Legitimate software using Python DLLs
52level: medium
References
Related rules
- APT27 - Emissary Panda Activity
- Aruba Network Service Potential DLL Sideloading
- DHCP Callout DLL Installation
- DHCP Server Error Failed Loading the CallOut DLL
- DHCP Server Loaded the CallOut DLL