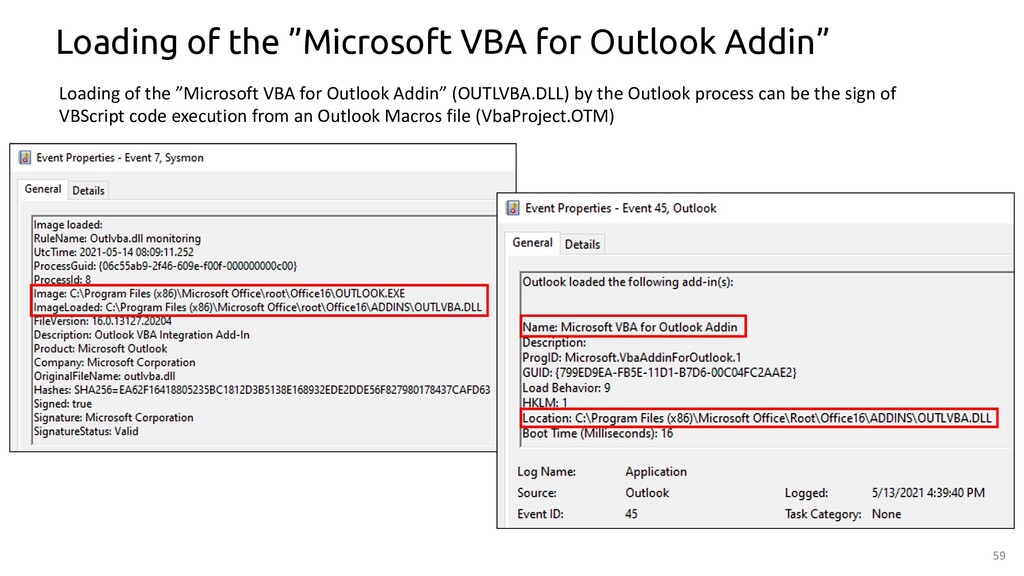
Microsoft VBA For Outlook Addin Loaded Via Outlook
Detects outlvba (Microsoft VBA for Outlook Addin) DLL being loaded by the outlook process
Sigma rule (View on GitHub)
1title: Microsoft VBA For Outlook Addin Loaded Via Outlook
2id: 9a0b8719-cd3c-4f0a-90de-765a4cb3f5ed
3status: test
4description: Detects outlvba (Microsoft VBA for Outlook Addin) DLL being loaded by the outlook process
5references:
6 - https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook?slide=58
7author: Nasreddine Bencherchali (Nextron Systems)
8date: 2023-02-08
9modified: 2024-03-12
10tags:
11 - attack.execution
12 - attack.t1204.002
13logsource:
14 category: image_load
15 product: windows
16detection:
17 selection:
18 Image|endswith: '\outlook.exe'
19 ImageLoaded|endswith: '\outlvba.dll'
20 condition: selection
21falsepositives:
22 - Legitimate macro usage. Add the appropriate filter according to your environment
23level: medium
References
Related rules
- CLR DLL Loaded Via Office Applications
- DotNET Assembly DLL Loaded Via Office Application
- Exploit for CVE-2017-0261
- Exploit for CVE-2017-8759
- Flash Player Update from Suspicious Location