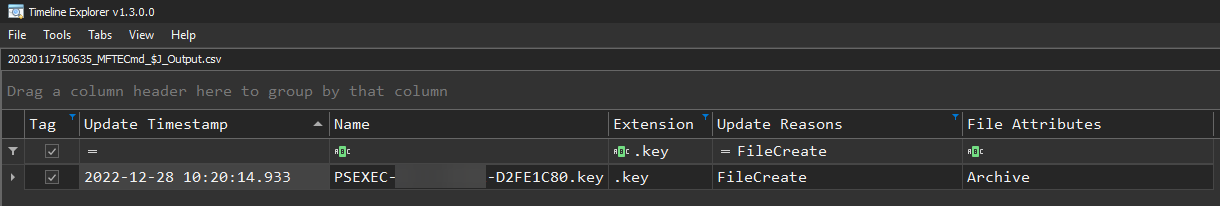
PSEXEC Remote Execution File Artefact
Detects creation of the PSEXEC key file. Which is created anytime a PsExec command is executed. It gets written to the file system and will be recorded in the USN Journal on the target system
Sigma rule (View on GitHub)
1title: PSEXEC Remote Execution File Artefact
2id: 304afd73-55a5-4bb9-8c21-0b1fc84ea9e4
3status: test
4description: Detects creation of the PSEXEC key file. Which is created anytime a PsExec command is executed. It gets written to the file system and will be recorded in the USN Journal on the target system
5references:
6 - https://aboutdfir.com/the-key-to-identify-psexec/
7 - https://twitter.com/davisrichardg/status/1616518800584704028
8author: Nasreddine Bencherchali (Nextron Systems)
9date: 2023-01-21
10modified: 2023-02-23
11tags:
12 - attack.lateral-movement
13 - attack.privilege-escalation
14 - attack.execution
15 - attack.persistence
16 - attack.t1136.002
17 - attack.t1543.003
18 - attack.t1570
19 - attack.s0029
20logsource:
21 category: file_event
22 product: windows
23detection:
24 selection:
25 TargetFilename|startswith: 'C:\Windows\PSEXEC-'
26 TargetFilename|endswith: '.key'
27 condition: selection
28falsepositives:
29 - Unlikely
30level: high
References
Related rules
- Audit CVE Event
- Azure Kubernetes CronJob
- Driver Load From A Temporary Directory
- Google Cloud Kubernetes CronJob
- HackTool - Default PowerSploit/Empire Scheduled Task Creation