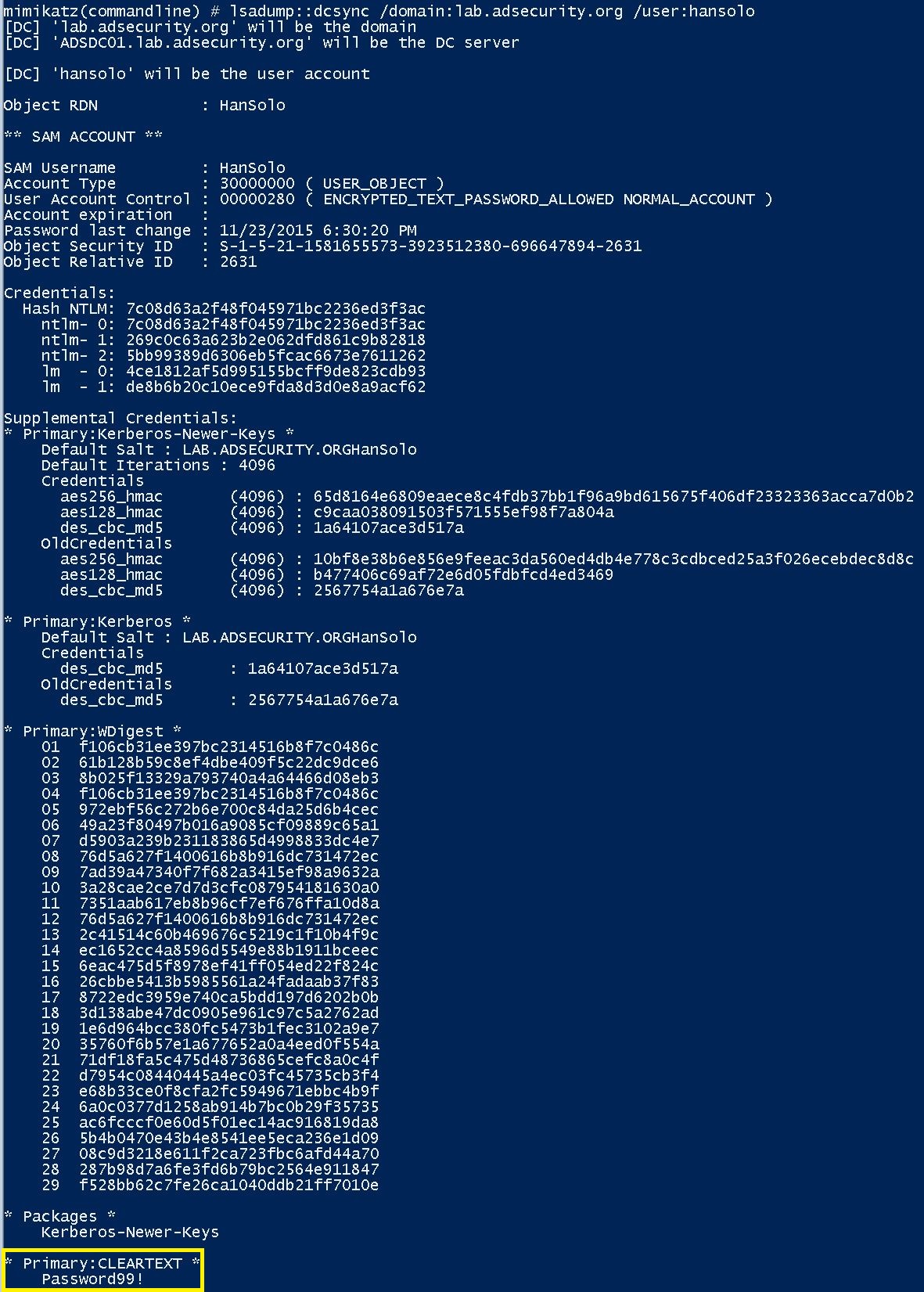
Weak Encryption Enabled and Kerberoast
Detects scenario where weak encryption is enabled for a user profile which could be used for hash/password cracking.
Sigma rule (View on GitHub)
1title: Weak Encryption Enabled and Kerberoast
2id: f6de9536-0441-4b3f-a646-f4e00f300ffd
3status: test
4description: Detects scenario where weak encryption is enabled for a user profile which could be used for hash/password cracking.
5references:
6 - https://adsecurity.org/?p=2053
7 - https://blog.harmj0y.net/redteaming/another-word-on-delegation/
8author: '@neu5ron'
9date: 2017-07-30
10modified: 2021-11-27
11tags:
12 - attack.defense-evasion
13 - attack.t1562.001
14logsource:
15 product: windows
16 service: security
17 definition: 'Requirements: Audit Policy : Account Management > Audit User Account Management, Group Policy : Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Account Management\Audit User Account Management'
18detection:
19 selection:
20 EventID: 4738
21 # According to Microsoft, the bit values are listed here: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4720
22 # However, that seems to be a simple copy from https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/useraccountcontrol-manipulate-account-properties
23 # and the actual flags that are used are quite different and, unfortunately, not documented.
24 # https://github.com/mdecrevoisier/EVTX-to-MITRE-Attack/ contains a number of EVTX files with relevant events, which can be used to extract
25 # the following values.
26 olduac_des: # 0x8000
27 OldUacValue|endswith:
28 - 8???
29 - 9???
30 - A???
31 - B???
32 - C???
33 - D???
34 - E???
35 - F???
36 newuac_des:
37 NewUacValue|endswith:
38 - 8???
39 - 9???
40 - A???
41 - B???
42 - C???
43 - D???
44 - E???
45 - F???
46 olduac_preauth: # 0x10000
47 OldUacValue|endswith:
48 - 1????
49 - 3????
50 - 5????
51 - 7????
52 - 9????
53 - B????
54 - D????
55 - F????
56 newuac_preauth:
57 NewUacValue|endswith:
58 - 1????
59 - 3????
60 - 5????
61 - 7????
62 - 9????
63 - B????
64 - D????
65 - F????
66 olduac_encrypted: # 0x800
67 OldUacValue|endswith:
68 - 8??
69 - 9??
70 - A??
71 - B??
72 - C??
73 - D??
74 - E??
75 - F??
76 newuac_encrypted:
77 NewUacValue|endswith:
78 - 8??
79 - 9??
80 - A??
81 - B??
82 - C??
83 - D??
84 - E??
85 - F??
86 condition: selection and ((newuac_des and not olduac_des) or (newuac_preauth and not olduac_preauth) or (newuac_encrypted and not olduac_encrypted))
87falsepositives:
88 - Unknown
89level: high
References
Related rules
- AMSI Bypass Pattern Assembly GetType
- AWS GuardDuty Important Change
- Azure Kubernetes Events Deleted
- Disable Exploit Guard Network Protection on Windows Defender
- Disable PUA Protection on Windows Defender