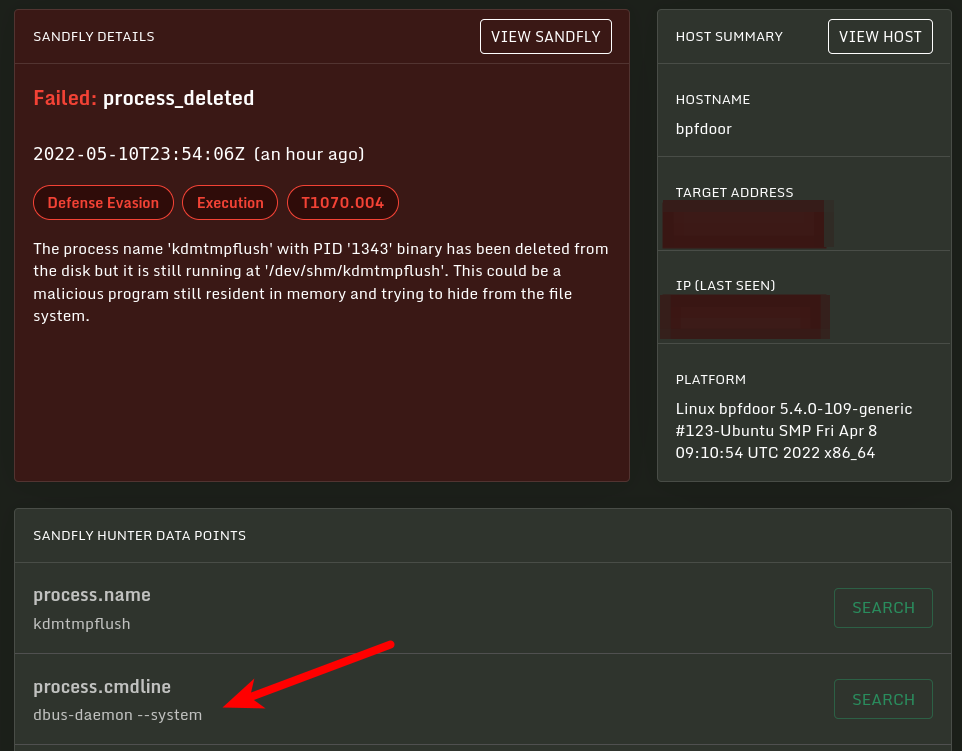
BPFDoor Abnormal Process ID or Lock File Accessed
detects BPFDoor .lock and .pid files access in temporary file storage facility
Sigma rule (View on GitHub)
1title: BPFDoor Abnormal Process ID or Lock File Accessed
2id: 808146b2-9332-4d78-9416-d7e47012d83d
3status: test
4description: detects BPFDoor .lock and .pid files access in temporary file storage facility
5references:
6 - https://www.sandflysecurity.com/blog/bpfdoor-an-evasive-linux-backdoor-technical-analysis/
7 - https://www.elastic.co/security-labs/a-peek-behind-the-bpfdoor
8author: Rafal Piasecki
9date: 2022-08-10
10tags:
11 - attack.execution
12 - attack.t1106
13 - attack.t1059
14logsource:
15 product: linux
16 service: auditd
17detection:
18 selection:
19 type: 'PATH'
20 name:
21 - /var/run/haldrund.pid
22 - /var/run/xinetd.lock
23 - /var/run/kdevrund.pid
24 condition: selection
25falsepositives:
26 - Unlikely
27level: high
References
Related rules
- Abusable DLL Potential Sideloading From Suspicious Location
- Add Insecure Download Source To Winget
- Add New Download Source To Winget
- Azure New CloudShell Created
- HackTool - CobaltStrike BOF Injection Pattern