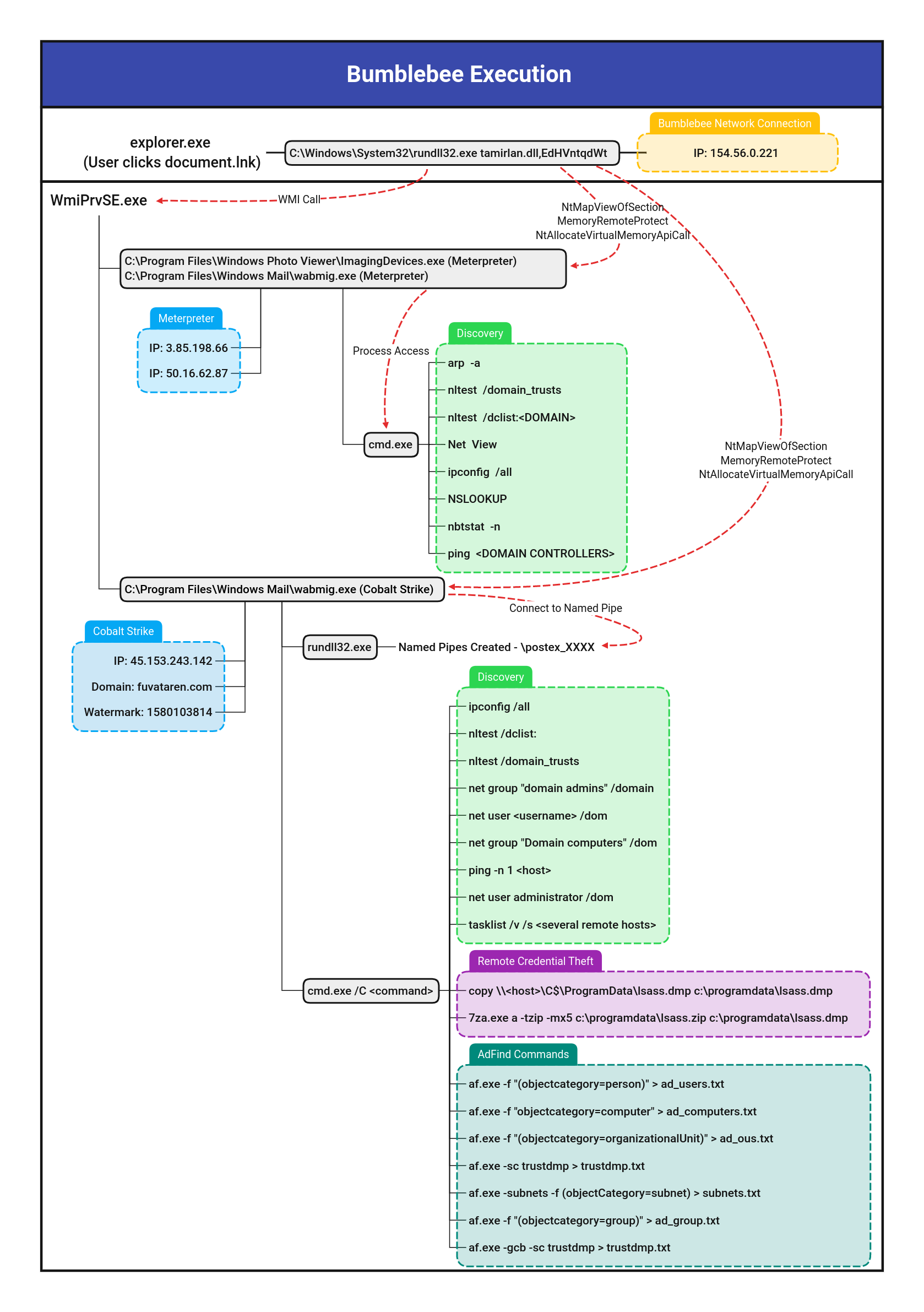
Potential Bumblebee Remote Thread Creation
Detects remote thread injection events based on action seen used by bumblebee
Sigma rule (View on GitHub)
1title: Potential Bumblebee Remote Thread Creation
2id: 994cac2b-92c2-44bf-8853-14f6ca39fbda
3status: test
4description: Detects remote thread injection events based on action seen used by bumblebee
5references:
6 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
7author: Nasreddine Bencherchali (Nextron Systems)
8date: 2022-09-27
9tags:
10 - attack.defense-evasion
11 - attack.execution
12 - attack.t1218.011
13 - attack.t1059.001
14 - detection.emerging-threats
15logsource:
16 product: windows
17 category: create_remote_thread
18detection:
19 selection:
20 SourceImage|endswith:
21 - '\wabmig.exe'
22 - '\wab.exe'
23 - '\ImagingDevices.exe'
24 TargetImage|endswith: '\rundll32.exe'
25 condition: selection
26falsepositives:
27 - Unknown
28level: high
References
Related rules
- APT29 2018 Phishing Campaign CommandLine Indicators
- Greenbug Espionage Group Indicators
- HTML Help HH.EXE Suspicious Child Process
- Potential Baby Shark Malware Activity
- Rorschach Ransomware Execution Activity