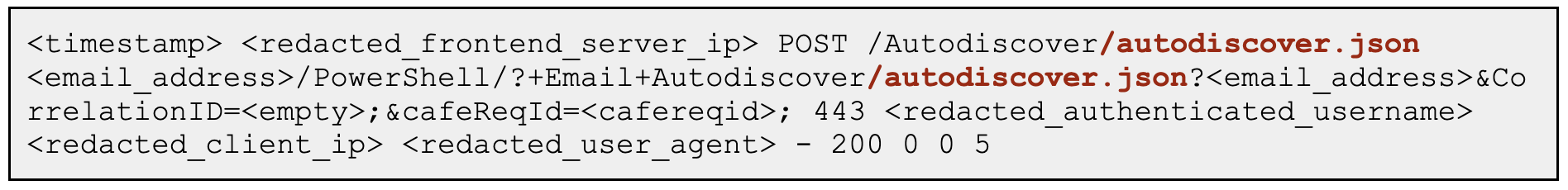
Potential OWASSRF Exploitation Attempt - Proxy
Detects exploitation attempt of the OWASSRF variant targeting exchange servers It uses the OWA endpoint to access the powershell backend endpoint
Sigma rule (View on GitHub)
1title: Potential OWASSRF Exploitation Attempt - Proxy
2id: 1ddf4596-1908-43c9-add2-1d2c2fcc4797
3status: test
4description: Detects exploitation attempt of the OWASSRF variant targeting exchange servers It uses the OWA endpoint to access the powershell backend endpoint
5references:
6 - https://www.crowdstrike.com/blog/owassrf-exploit-analysis-and-recommendations/
7 - https://www.rapid7.com/blog/post/2022/12/21/cve-2022-41080-cve-2022-41082-rapid7-observed-exploitation-of-owassrf-in-exchange-for-rce/
8author: Nasreddine Bencherchali (Nextron Systems)
9date: 2022-12-22
10tags:
11 - attack.initial-access
12 - attack.t1190
13 - detection.emerging-threats
14logsource:
15 category: proxy
16detection:
17 selection:
18 cs-method: 'POST'
19 sc-status: 200
20 c-uri|contains|all:
21 - '/owa/'
22 - '/powershell'
23 c-uri|contains:
24 - '@'
25 - '%40'
26 filter_main_ua:
27 c-useragent:
28 - 'ClientInfo'
29 - 'Microsoft WinRM Client'
30 - 'Exchange BackEnd Probes'
31 condition: selection and not 1 of filter_main_*
32falsepositives:
33 - Web vulnerability scanners
34level: high
References
Related rules
- CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Linux)
- CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Windows)
- CVE-2023-22518 Exploitation Attempt - Vulnerable Endpoint Connection (Proxy)
- CVE-2023-22518 Exploitation Attempt - Vulnerable Endpoint Connection (Webserver)
- CVE-2023-46747 Exploitation Activity - Proxy