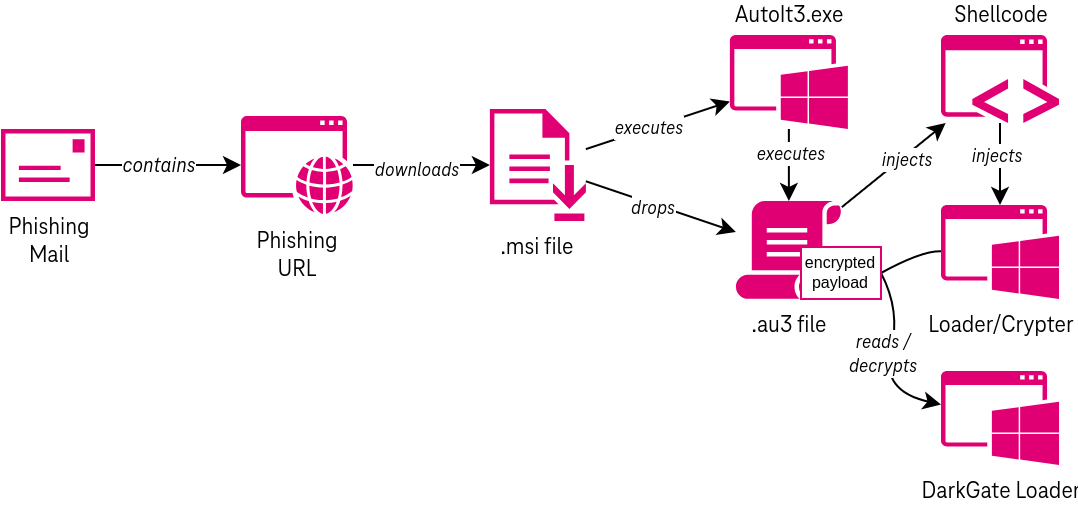
Autoit3.exe Executable File Creation Matching DarkGate Behavior
Detects the usage of curl.exe, KeyScramblerLogon, or other non-standard/suspicious processes used to create Autoit3.exe. This activity has been associated with DarkGate malware, which uses Autoit3.exe to execute shellcode that performs process injection and connects to the DarkGate command-and-control server. Curl, KeyScramblerLogon, and these other processes consitute non-standard and suspicious ways to retrieve the Autoit3 executable.
Sigma rule (View on GitHub)
1title: Autoit3.exe Executable File Creation Matching DarkGate Behavior
2id: 1a433e1d-03d2-47a6-8063-ece992cf4e73
3status: experimental
4description: |
5 Detects the usage of curl.exe, KeyScramblerLogon, or other non-standard/suspicious processes used to create Autoit3.exe.
6 This activity has been associated with DarkGate malware, which uses Autoit3.exe to execute shellcode that performs
7 process injection and connects to the DarkGate command-and-control server. Curl, KeyScramblerLogon, and these other
8 processes consitute non-standard and suspicious ways to retrieve the Autoit3 executable.
9references:
10 - Internal Research
11 - https://github.security.telekom.com/2023/08/darkgate-loader.html
12 - https://www.kroll.com/en/insights/publications/cyber/microsoft-teams-used-as-initial-access-for-darkgate-malware
13 - https://github.com/pr0xylife/DarkGate/tree/main
14author: Micah Babinski
15date: 2023/10/11
16tags:
17 - attack.command_and_control
18 - attack.execution
19 - attack.t1105
20 - attack.t1059
21logsource:
22 category: file_event
23 product: windows
24detection:
25 selection:
26 Image|endswith:
27 - '\curl.exe'
28 - '\KeyScramblerLogon.exe'
29 - '\Autoit3.exe'
30 - '\wmprph.exe'
31 - '\ExtExport.exe'
32 TargetFilename|endswith: '\Autoit3.exe'
33 condition: selection
34falsepositives:
35 - Unknown
36level: medium```
References
Related rules
- DarkGate Autoit3.exe Execution Parameters
- BITSAdmin Downloading Malicious Binaries (RedCanary Threat Detection Report)
- Certutil Downloading Malicious Binaries (RedCanary Threat Detection Report)
- Possible Raspberry Robin DLL Download Using msiexec (RedCanary Threat Detection Report)
- Quick Execution of a Series of Suspicious Commands