Potential Direct Kubelet Access via Process Arguments Detected via Defend for Containers
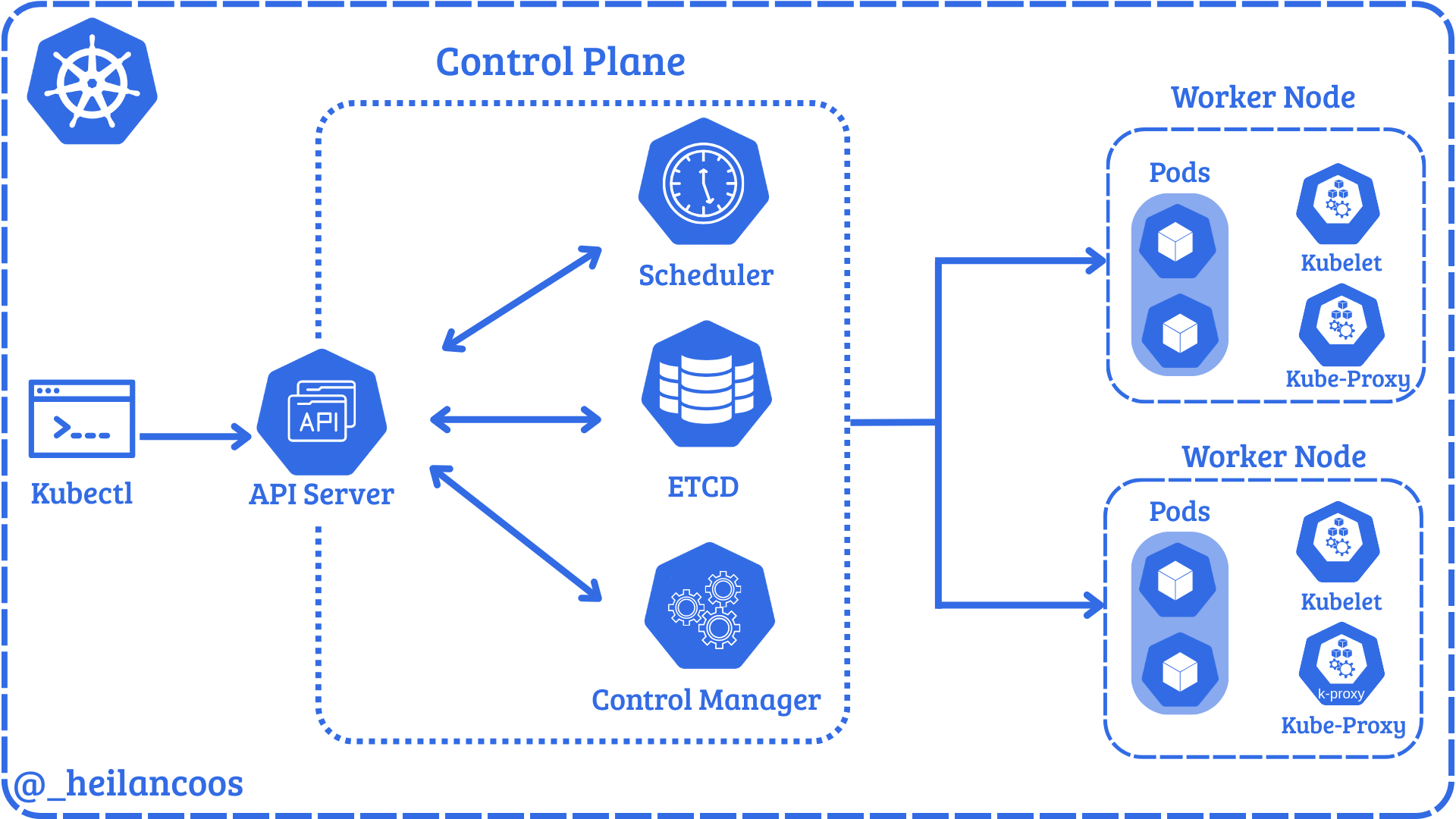
This rule detects potential direct Kubelet access via process arguments. An adversary may need to access the Kubelet API to gain access to the Kubernetes API server or other resources within the cluster. These requests are often used to enumerate or execute commands on the Kubernetes API server or other resources within the cluster, and may indicate an attempt to move laterally within the cluster.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2026/02/02"
3integration = ["cloud_defend"]
4maturity = "production"
5min_stack_comments = "Defend for Containers integration was re-introduced in 9.3.0"
6min_stack_version = "9.3.0"
7updated_date = "2026/02/09"
8
9[rule]
10author = ["Elastic"]
11description = """
12This rule detects potential direct Kubelet access via process arguments. An adversary may need to access the
13Kubelet API to gain access to the Kubernetes API server or other resources within the cluster. These requests
14are often used to enumerate or execute commands on the Kubernetes API server or other resources within the
15cluster, and may indicate an attempt to move laterally within the cluster.
16"""
17from = "now-6m"
18index = ["logs-cloud_defend.process*"]
19interval = "5m"
20language = "eql"
21license = "Elastic License v2"
22name = "Potential Direct Kubelet Access via Process Arguments Detected via Defend for Containers"
23note = """ ## Triage and analysis
24
25> **Disclaimer**:
26> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
27
28### Investigating Potential Direct Kubelet Access via Process Arguments Detected via Defend for Containers
29
30This detection flags an interactive process started inside a Linux container that includes an HTTP request targeting the Kubelet API on port 10250, a common pivot point for gaining execution and visibility across nodes. Attackers use direct Kubelet access to enumerate pods, fetch logs, or run commands that can lead to broader cluster access and lateral movement. A typical pattern is invoking curl or wget from a container shell against `https://<node-ip>:10250/` endpoints to probe or execute actions.
31
32### Possible investigation steps
33
34- Identify the originating pod/workload and container image for the interactive session, then determine whether the container was expected to provide diagnostic tooling or shell access and whether it recently changed.
35- Extract the full command line and reconstruct the requested Kubelet endpoint path (for example `/pods`, `/exec`, `/run`, `/logs`) to infer intent (enumeration vs remote execution) and capture any embedded tokens or client cert usage.
36- Correlate the process start time with Kubernetes audit logs and API server events to see if there were concurrent pod exec/attach, secret reads, or workload modifications suggesting follow-on activity.
37- Verify whether the destination node IP/hostname is the local node or a remote node and review network flow logs/egress policies to confirm the container could reach port 10250 and whether other nodes were contacted.
38- Check node and Kubelet configuration for exposure and auth bypass risk (anonymous auth, webhook mode, client certs), and inspect Kubelet logs around the timestamp for the corresponding request and response status codes.
39
40### False positive analysis
41
42- A cluster operator or SRE opens an interactive shell in a troubleshooting container and manually curls `https://<node-ip>:10250/` (or `/pods`/`/metrics`) to validate Kubelet reachability, authentication behavior, or node health during incident triage.
43- A legitimate in-container diagnostic workflow uses an interactive session to probe the local node’s Kubelet port 10250 for environment verification (e.g., confirming node IP mapping or TLS/cert configuration), embedding the URL in process arguments without any intent to enumerate or execute actions across the cluster.
44
45### Response and remediation
46
47- Isolate the affected pod by removing service exposure and applying a temporary egress deny rule to block traffic to node port 10250 from that namespace/pod label, then terminate the interactive shell session and restart the workload from a known-good image.
48- Capture and preserve the full command line, container filesystem changes, and relevant Kubelet and Kubernetes audit log entries around the timestamp, then hunt for additional in-cluster attempts to reach `https://<node>:10250/` from other pods or namespaces.
49- Rotate any credentials that may have been exposed or used (service account tokens, client certificates, kubeconfig files) and revoke or redeploy affected service accounts, then validate no unauthorized `exec/attach`, secret reads, or workload changes occurred after the access attempt.
50- Escalate to the platform security/on-call incident commander immediately if the Kubelet request targeted sensitive endpoints like `/exec`, `/run`, `/containerLogs`, or returned successful responses (2xx/3xx) or if similar commands are seen across multiple nodes.
51- Harden by enforcing Kubelet authentication/authorization (disable anonymous access, require webhook authz, restrict client cert issuance), and implement network controls that prevent pods from reaching node Kubelet ports except from approved node-local agents.
52- Reduce recurrence by removing shell and HTTP tooling from application images, limiting interactive access (disable `kubectl exec` for non-admins), and tightening RBAC and admission policies to block privileged pods/host networking that increase node API reachability.
53"""
54references = [
55 "https://heilancoos.github.io/research/2025/12/16/kubernetes.html#kubelet-api",
56 "https://www.cyberark.com/resources/threat-research-blog/using-kubelet-client-to-attack-the-kubernetes-cluster",
57 "https://www.aquasec.com/blog/kubernetes-exposed-exploiting-the-kubelet-api/"
58]
59risk_score = 47
60rule_id = "b4bd186b-69c6-45ad-8bef-5c35bbadeaef"
61severity = "medium"
62tags = [
63 "Data Source: Elastic Defend for Containers",
64 "Domain: Container",
65 "OS: Linux",
66 "Use Case: Threat Detection",
67 "Tactic: Execution",
68 "Tactic: Discovery",
69 "Resources: Investigation Guide",
70]
71timestamp_override = "event.ingested"
72type = "eql"
73query = '''
74process where host.os.type == "linux" and event.type == "start" and event.action == "exec" and
75process.args like "http*:10250*" and process.interactive == true and container.id like "?*"
76'''
77
78[[rule.threat]]
79framework = "MITRE ATT&CK"
80
81[[rule.threat.technique]]
82id = "T1059"
83name = "Command and Scripting Interpreter"
84reference = "https://attack.mitre.org/techniques/T1059/"
85
86[[rule.threat.technique.subtechnique]]
87id = "T1059.004"
88name = "Unix Shell"
89reference = "https://attack.mitre.org/techniques/T1059/004/"
90
91[rule.threat.tactic]
92id = "TA0002"
93name = "Execution"
94reference = "https://attack.mitre.org/tactics/TA0002/"
95
96[[rule.threat]]
97framework = "MITRE ATT&CK"
98
99[[rule.threat.technique]]
100id = "T1613"
101name = "Container and Resource Discovery"
102reference = "https://attack.mitre.org/techniques/T1613/"
103
104[rule.threat.tactic]
105id = "TA0007"
106name = "Discovery"
107reference = "https://attack.mitre.org/tactics/TA0007/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Potential Direct Kubelet Access via Process Arguments Detected via Defend for Containers
This detection flags an interactive process started inside a Linux container that includes an HTTP request targeting the Kubelet API on port 10250, a common pivot point for gaining execution and visibility across nodes. Attackers use direct Kubelet access to enumerate pods, fetch logs, or run commands that can lead to broader cluster access and lateral movement. A typical pattern is invoking curl or wget from a container shell against https://<node-ip>:10250/ endpoints to probe or execute actions.
Possible investigation steps
- Identify the originating pod/workload and container image for the interactive session, then determine whether the container was expected to provide diagnostic tooling or shell access and whether it recently changed.
- Extract the full command line and reconstruct the requested Kubelet endpoint path (for example
/pods,/exec,/run,/logs) to infer intent (enumeration vs remote execution) and capture any embedded tokens or client cert usage. - Correlate the process start time with Kubernetes audit logs and API server events to see if there were concurrent pod exec/attach, secret reads, or workload modifications suggesting follow-on activity.
- Verify whether the destination node IP/hostname is the local node or a remote node and review network flow logs/egress policies to confirm the container could reach port 10250 and whether other nodes were contacted.
- Check node and Kubelet configuration for exposure and auth bypass risk (anonymous auth, webhook mode, client certs), and inspect Kubelet logs around the timestamp for the corresponding request and response status codes.
False positive analysis
- A cluster operator or SRE opens an interactive shell in a troubleshooting container and manually curls
https://<node-ip>:10250/(or/pods//metrics) to validate Kubelet reachability, authentication behavior, or node health during incident triage. - A legitimate in-container diagnostic workflow uses an interactive session to probe the local node’s Kubelet port 10250 for environment verification (e.g., confirming node IP mapping or TLS/cert configuration), embedding the URL in process arguments without any intent to enumerate or execute actions across the cluster.
Response and remediation
- Isolate the affected pod by removing service exposure and applying a temporary egress deny rule to block traffic to node port 10250 from that namespace/pod label, then terminate the interactive shell session and restart the workload from a known-good image.
- Capture and preserve the full command line, container filesystem changes, and relevant Kubelet and Kubernetes audit log entries around the timestamp, then hunt for additional in-cluster attempts to reach
https://<node>:10250/from other pods or namespaces. - Rotate any credentials that may have been exposed or used (service account tokens, client certificates, kubeconfig files) and revoke or redeploy affected service accounts, then validate no unauthorized
exec/attach, secret reads, or workload changes occurred after the access attempt. - Escalate to the platform security/on-call incident commander immediately if the Kubelet request targeted sensitive endpoints like
/exec,/run,/containerLogs, or returned successful responses (2xx/3xx) or if similar commands are seen across multiple nodes. - Harden by enforcing Kubelet authentication/authorization (disable anonymous access, require webhook authz, restrict client cert issuance), and implement network controls that prevent pods from reaching node Kubelet ports except from approved node-local agents.
- Reduce recurrence by removing shell and HTTP tooling from application images, limiting interactive access (disable
kubectl execfor non-admins), and tightening RBAC and admission policies to block privileged pods/host networking that increase node API reachability.
References
Related rules
- Potential Kubeletctl Execution Detected via Defend for Containers
- Kubernetes Direct API Request via Curl or Wget
- Direct Interactive Kubernetes API Request Detected via Defend for Containers
- Direct Interactive Kubernetes API Request by Common Utilities
- Direct Interactive Kubernetes API Request by Unusual Utilities