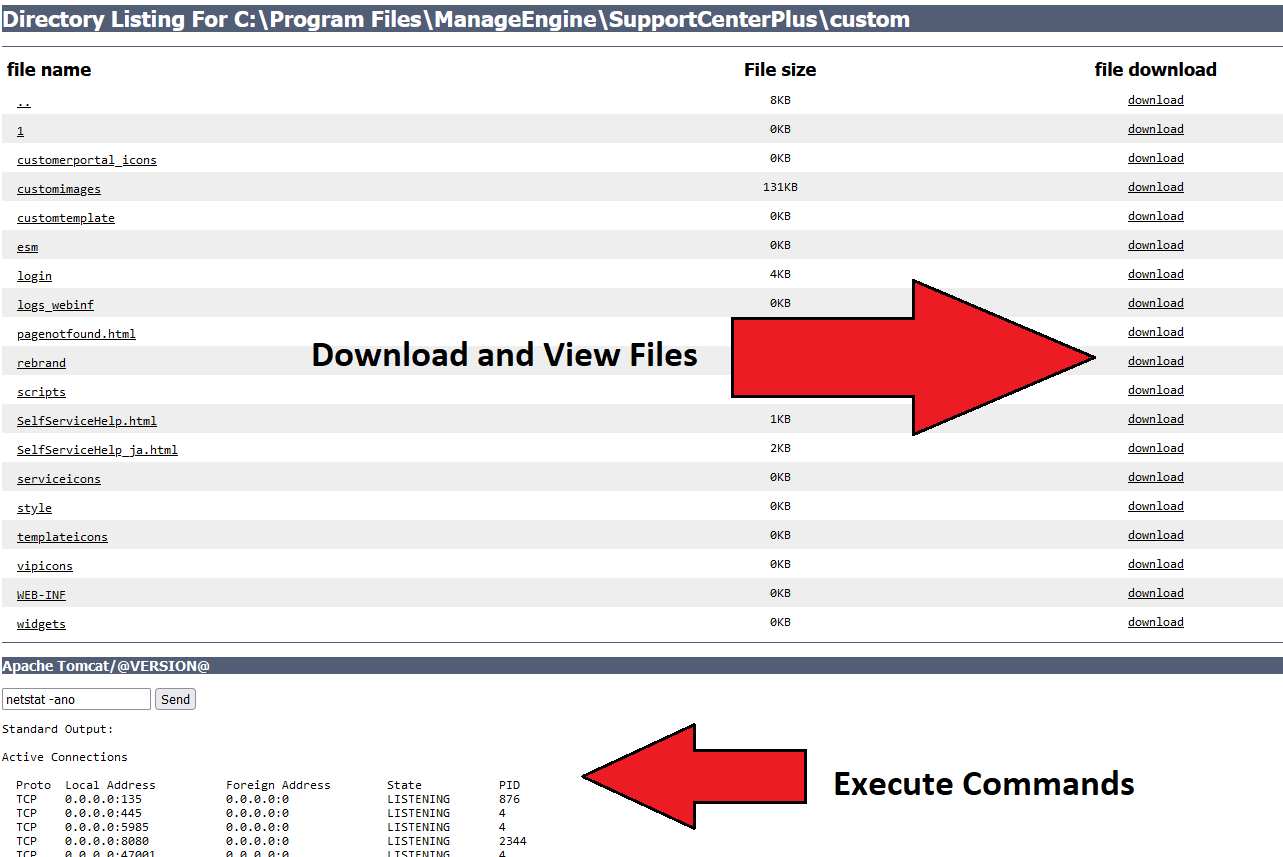
Webshell Usage with ManageEngine Product
Detection of a webshell in a ManageEngine internet accessible directory.
Sigma rule (View on GitHub)
1title: Webshell Usage with ManageEngine Product
2id: c1717e0b-e364-4032-bb8e-1bd112ba4058
3status: experimental
4description: Detection of a webshell in a ManageEngine internet accessible directory.
5author: iiamaleks,TheDFIRReport
6date: 2022/06/06
7modified: 2023/01/08
8references:
9 - https://thedfirreport.com/2022/06/06/will-the-real-msiexec-please-stand-up-exploit-leads-to-data-exfiltration/
10logsource:
11 product: zeek
12 service: http
13detection:
14 port:
15 destination_port: 8080
16 webshell_url_path:
17 - url_original|contains:
18 - '/custom/login/*.jsp'
19 webshell_paramters:
20 - url_original|contains:
21 - '?file='
22 - '&data='
23 - '&action='
24 - '&p='
25 condition: port and webshell_url_path and webshell_paramters
26falsepositives:
27 - Web application using the same file path, file name, and GET parameters as described in this rule.
28level: high
29tags:
30 - attack.persistence
31 - attack.t1505.003
References
Related rules
- Webshell Remote Command Execution
- Scheduled task executing powershell encoded payload from registry
- Suspicious Commands by SQL Server
- Cisco Local Accounts
- Cisco Modify Configuration