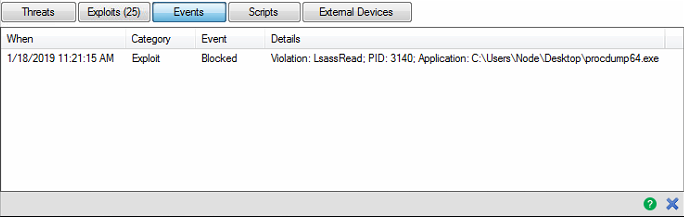
Suspicious Unsigned Dbghelp/Dbgcore DLL Loaded
Detects the load of dbghelp/dbgcore DLL (used to make memory dumps) by suspicious processes. Tools like ProcessHacker and some attacker tradecract use MiniDumpWriteDump API found in dbghelp.dll or dbgcore.dll. As an example, SilentTrynity C2 Framework has a module that leverages this API to dump the contents of Lsass.exe and transfer it over the network back to the attacker's machine.
Sigma rule (View on GitHub)
1title: Suspicious Unsigned Dbghelp/Dbgcore DLL Loaded
2id: bdc64095-d59a-42a2-8588-71fd9c9d9abc
3related:
4 - id: 0e277796-5f23-4e49-a490-483131d4f6e1 # Suspicious Loading
5 type: similar
6status: test
7description: |
8 Detects the load of dbghelp/dbgcore DLL (used to make memory dumps) by suspicious processes.
9 Tools like ProcessHacker and some attacker tradecract use MiniDumpWriteDump API found in dbghelp.dll or dbgcore.dll.
10 As an example, SilentTrynity C2 Framework has a module that leverages this API to dump the contents of Lsass.exe and transfer it over the network back to the attacker's machine.
11references:
12 - https://docs.microsoft.com/en-us/windows/win32/api/minidumpapiset/nf-minidumpapiset-minidumpwritedump
13 - https://www.pinvoke.net/default.aspx/dbghelp/MiniDumpWriteDump.html
14 - https://medium.com/@fsx30/bypass-edrs-memory-protection-introduction-to-hooking-2efb21acffd6
15author: Perez Diego (@darkquassar), oscd.community, Ecco
16date: 2019/10/27
17modified: 2022/12/09
18tags:
19 - attack.credential_access
20 - attack.t1003.001
21logsource:
22 category: image_load
23 product: windows
24detection:
25 selection:
26 ImageLoaded|endswith:
27 - '\dbghelp.dll'
28 - '\dbgcore.dll'
29 Signed: 'false'
30 condition: selection
31falsepositives:
32 - Unknown
33level: high
References
Related rules
- SafetyKatz Default Dump Filename
- HackTool - CreateMiniDump Execution
- HackTool - Dumpert Process Dumper Execution
- Mimikatz Use
- PowerShell Get-Process LSASS in ScriptBlock